Addressing the Challenges of Securing Hybrid Cloud Access: What You Need to Know
Author(s):
Joseph Carson, Chief Security Scientist & Advisory CISO, Delinea
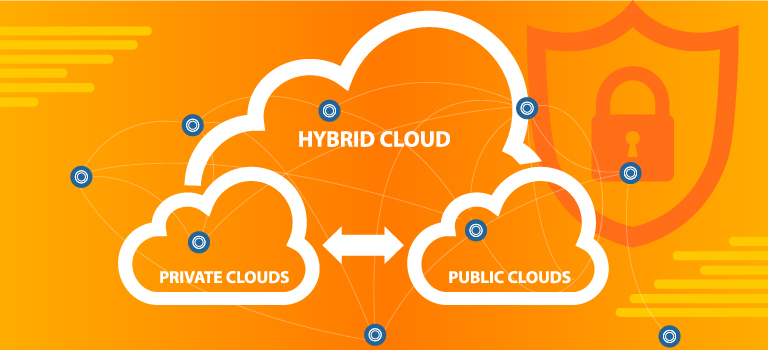
For a growing number of companies, a blend of public cloud services, private clouds, and on-premises infrastructure offer the best solution to the benefits and limitations of each. Cloud adoption is growing, and the past two years have shown a major increase in the use of cloud services. In addition, emerging technologies like edge computing … Read more