The Darkest of the Dark: The 764 Network
Is Your Password in the Green? Modern Tips for Maximum Security
The CSO Conference & Awards: A Brief History
Blockchain Technology: From Hype to The Future
Tools to Meet Tomorrow’s Mobile Cybersecurity Threats for Government
{Latest Posts}

The Consequences of Digital Piracy
Digital content can be quite expensive. Especially when you get into the high-end software packages. Sometimes this content costs several thousand dollars. But not everyone can afford these prices. If you have spent any amount

Defense Against Man-In-The-Middle Attacks (MITM)
What You Need For The Best Defense Against Man-In-The-Middle (MITM) Attacks Man-in-the-middle (MITM) attacks involve the interception of communication between two or more digital systems. Because of this, they are both difficult to detect and

Multi-factor Authentication (MFA) is the Future
Going the Extra Mile Passwords are now becoming a thing of the past. Multi-factor authentication, or MFA, is viewed as the solution to passwords. MFA is a method of identifying yourself through a variety of

“DND”-R: Giving your Disaster Recovery Strategy a Dungeon Master.
Disaster Recovery (DR) has always been a very comprehensive and multi-departmental undertaking. This has only increased in connectivity in the digital age. With so many devices being connected to the network now, it is beyond

How to Stop Everyone From Stealing Your Content
Face it. Some people hate paying to watch the latest film or TV episode. Be it a lack of accessibility or a lack of funds, many people will do anything to see content for free.

App Access: Life Invasion
Life Invasion: Your Privacy A problem that has been occurring for years is finally generating concern. 77% of Americans own smart phones. Majority of those people make the mistake of allowing apps such as Facebook
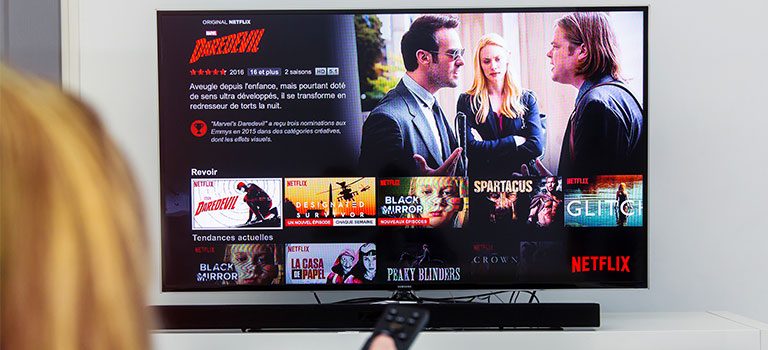
The Netflix Sharing Problem
Netflix Has a Problem With Password Sharing. We have all heard the story of the college grad using his former roommate’s parents’ Netflix password. We all know the ex-boyfriend binging his favorite shows with his

The Dark Side of AI
The rise of AI is as inevitable as the next data breach. The 21st century has seen a massive resurgence in highly advanced AI usage techniques. We can now process large amounts of data in






