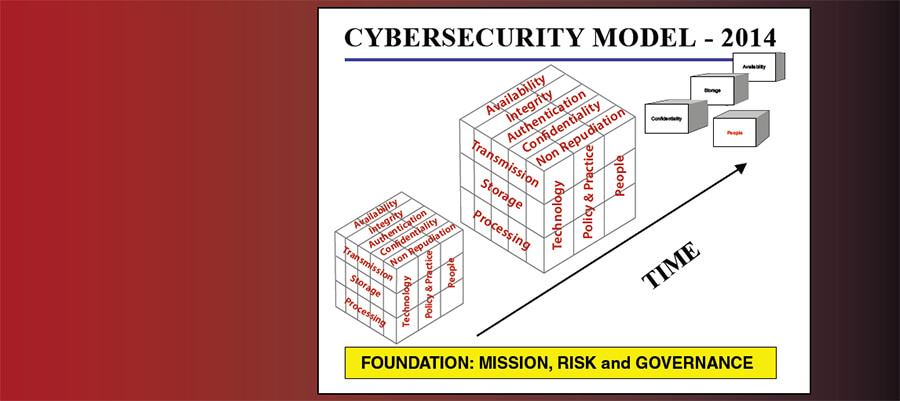
Cybersecurity & The Modern World
Cognitive Computing for Business Insights and Gains
Author(s):
Pratik Gundawar, ,
We live in an age where logical reasoning matters the most, whether we use apps on smartphones for weather forecast, or software for improving driving. Ever since the invention of computers, we have grown to expect larger-than-life outputs from them. Computers must handle our basic day-to-day chores as well as solve complex problems. The race … Read more