The long-term success of any business or digital venture depends solely on a strong software architecture – one that has robust performance and is equipped with foolproof cybersecurity. In simpler terms, software architecture forms the basis of the development of an enterprise. Therefore, the main source acts as a guideline to shape the future of the company.
What is Software Architecture
Software architecture is the main tool for crafting a robust cybersecurity plan that helps attract users toward the system. Additionally, it guarantees top notch user experience, due to a high level of protection and vigilance.
Software architecture helps IT professionals to see the core developments of the system, and hence, make decisions that have an impact on the organization. These core technologies could help make or break a system.
What is Cybersecurity & Why is it Important
Software architecture is the ultimate resource for handling communication and action-oriented decisions among users, customers, and third parties.
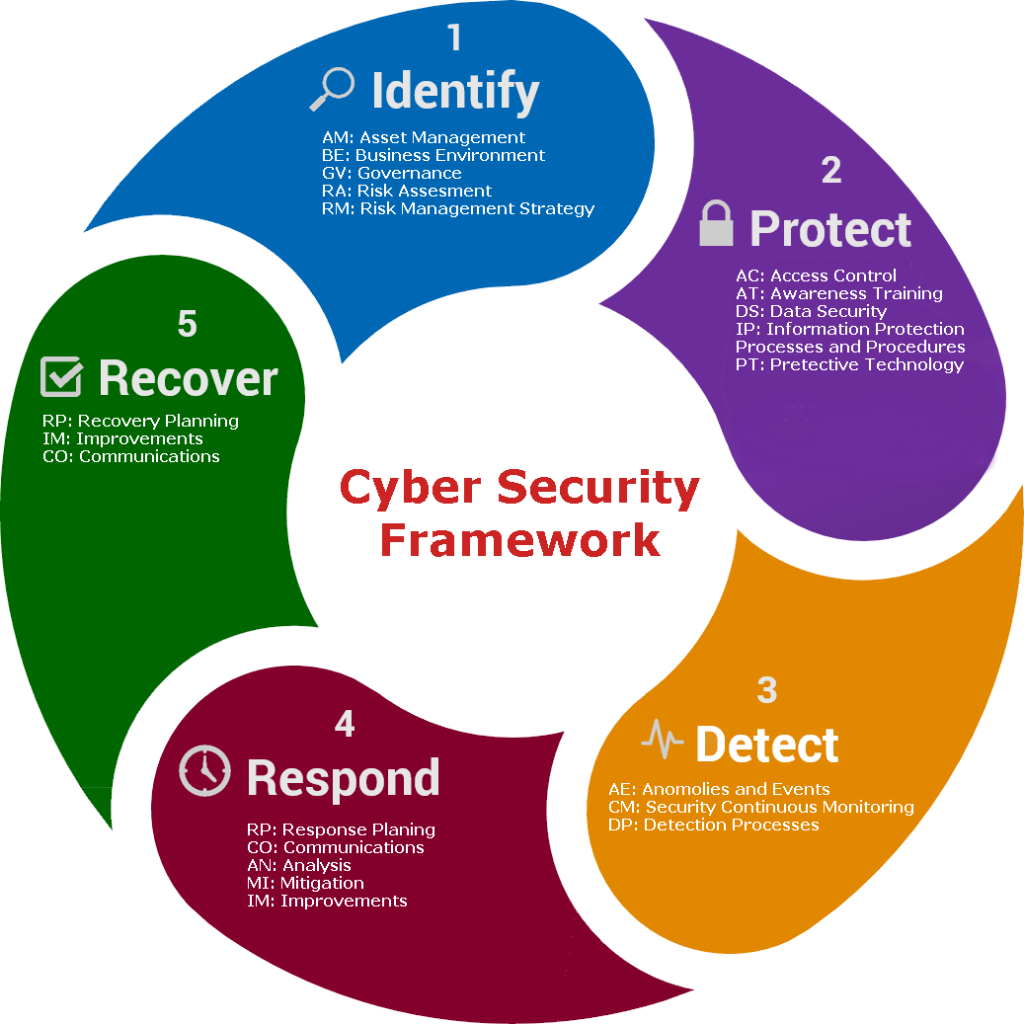
For users to download and consequently use your program, you need to introduce foolproof cyber security services in your system’s software architecture. This will ensure timely counter-intuitive attacks to the threats imposed. For your software architecture to have a robust cybersecurity model, you need to incorporate security processes. Additionally, you need to incorporate analytics and collaborative functions that act to prevent user complexity.
Incorporating your system with strong software architecture also improves the quality of the system. For example, below are our four reasons to help you understand the importance of software architecture in foolproof cybersecurity for your business/organization.
1) Strong Cybersecurity = Low System Vulnerability
Approximately 360,000 new files of malware pose a threat to your system every day. Apart from these daily threats, you would not know about the pre-existing files of malware that your system already has. In addition to malware such as ransomware, worms and Trojans, different unpatched vulnerabilities can cause your entire system to fail.
Around $1.3 million is lost per data breach by enterprises and small-and-medium business (SMBs) in North America, according to CSO Online. However, your system can prevent such attacks by reinforcing and incorporating foolproof cybersecurity practices into your system’s software architecture.
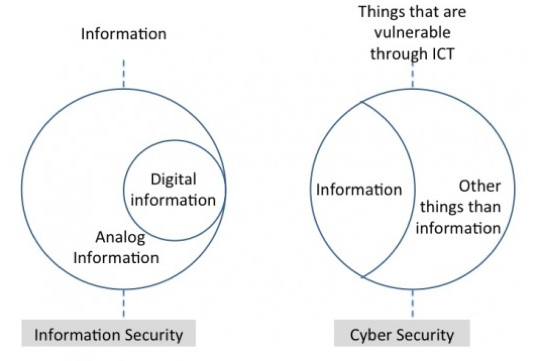
The whole idea of incorporating foolproof cybersecurity technology is to prevent your system’s vulnerability to attacks. Unfortunately, this often comes with a price. The cost of preventing a potential security threat to the system might cost up to $100,000 which can certainly lead you into unwanted financial liabilities.
However, if you tend to look at the concerns deeply, you do not exactly know about the details of the malware your system is exposed to. Therefore, by preventing a preceding threat to the system, you are not only helping to prevent a much bigger lash out to the system, but also preventing a major data breach.
For a more promising yet strong software architecture, there are different security tools that not only help to prevent an attack to the system, but also allow you to look into the details of each plausible threat.
One such tool is the Security Information and Event Management (SIEM) software that can help software architects improve the ROI of the system.
This tool allows you to record the quantity of the attacks your system was exposed to so you can make timely amends to your cybersecurity protocol. Additionally, this lets you determine the efficiency of each counterattack and helps identify the flaws in the system.
2) Security Architecture in Handling Key Data Standards
For an organization to function, several data standards need to be in place to protect user information. Some of these have been in use by insurance and healthcare providers such as the Health Insurance Portability and Accountability Act (HIPAA). In contrast, there are others such as the Payment Card Industry Data Security Standard that keeps a check and balance on credit and debit card information.
Apart from the major security standards, others keep a check on the rights of clients and ensure safety of their data. Indeed, these data security standards help ensure the protection of collected data by preventing malware and anomalies from acquiring personal information from online resources.
To incorporate these data security standards in your system, you need to design and infuse certain measures in your software architecture. Therefore, these measures will act as tools and require multi-factor authentication (MFA) processes to gain access to administrative authorities.
Similarly, strong security architecture is also subject to change in response to certain malware exposure. As a result, this allows the software architecture to alter and update its intricacies to meet the requirements. This is so that it can counterattack the threats and enact optimum security measures in need.
3) Foolproof Cybersecurity Helps Maintain Business Partnerships
Gaining the trust of third parties is highly essential to attract potential leads to a business. However, at times, businesses tend to give unsolicited access to third parties to gain their trust for a potential partnership. In that case, might seem as one of the major practices that require networking. But it can prove to be a threat to your company. Such security breaches can cripple your entire system, especially in the absence of a strong security architecture.

For instance, in 2013, Target Inc. received a major blow to its networking operations. Target had granted back-end access to a third-party vendor. This third party vendor, Fazio Mechanical Services, had been in charge for the provision of optimum refrigeration services and installation of HVAC systems in several outlets of the retailer. The attackers approached Target by stealing several user-based credentials and networking information from the vendor. As a result, this compromised the identity of millions of customers. Additionally, it caused the company to suffer from identity theft due to the security breach.
Giving access to third-party vendors is sometimes necessary for building connections and smooth operations. While the third parties might not be involved in security breaches, there is a possibility that it still might. On the other hand, there is also a possibility that by giving access to third parties, you are exposing your system to the bugs and anomalies present in their system. This could make your organization more prone to a cybersecurity breach.
It is essential to gather significant proof and data regarding the software architecture of your networking connections. It is also essential to prevent data leaks from a possible merger on your side. In order to prevent this, incorporate strong security architecture so that you can compete in the market against major companies and vendors.
Strong software architecture will also help you make robust connections that operate on trust and leadership. This will help strengthen your presence in the networking community, therefore, allowing you to attract and garner leads with foolproof cybersecurity.
4) Prevents Losses and Helps Increase Revenue
Following the major security breach in 2013, Target suffered an exponential loss in business due to identity theft and surplus charges. According to The New York Times, Target suffered a 40% blow in its quarterly profit – which not only led the company to break ties with its vendors – but also with its long-lasting customers.
In order to prevent significant loss in businesses, it is essential to incorporate robust security measures so that your company remains protected amidst several security threats. Security breaches are not only bad for publicity, but are also vicious for the business. It causes businesses to lose their relationships with companies and impact revenue.
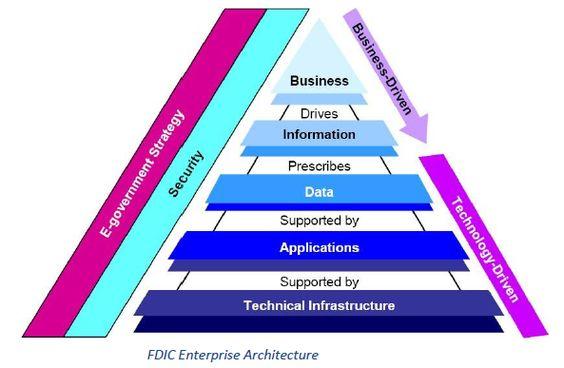
Strong cybersecurity measures can not only help companies to prioritize their goals in the market, but will also help them to grow exponentially amidst competition. Cybersecurity is essential for a company to adapt to technical changes in order to meet several operational requirements and legislative queries. Strong software architecture therefore, helps to establish a foolproof cybersecurity system that not only prevents consequent attacks, but also improves the quality, development, and manageability of the entire operation.
Tags: Cybersecurity, data breach, Ransomware, Software, Software Architecture, Target, Trojan


