Feature Article
CYBERMARYLAND: Making Connections for Business
Author(s):
Erika Butler, , United States Cybersecurity Magazine
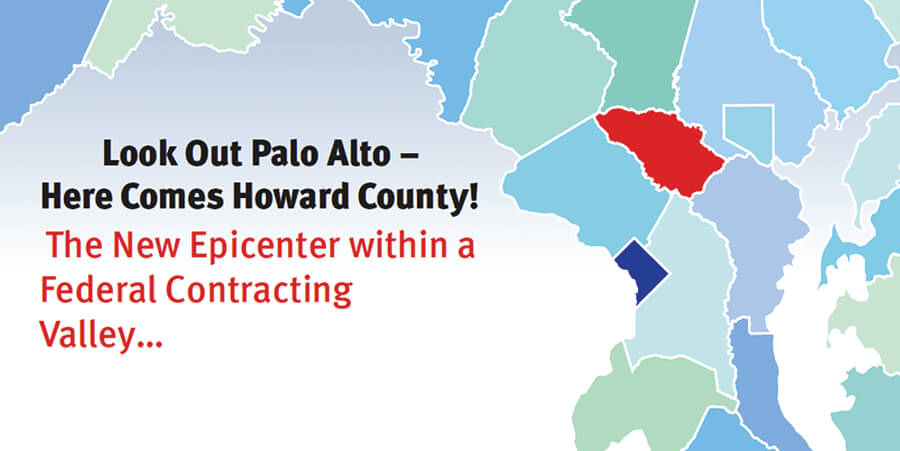
Ten years ago, information security meant installing Norton on a laptop. Today it has evolved into a much broader concept, an entire industry aimed at protecting information. “Now it’s that times 100,000” said Ursula Powidzki, Assistant Secretary of Business and Enterprise Development for the Maryland Department of Business and Economic Development, “because increasingly everything is … Read more