Red lights, yellow lights, green lights. A flashing light? A traffic warning sign? Recognized as a critical infrastructure by the Department of Homeland Security (DHS), the transportation system is essential to modern life. From the skies to the seas to the railways to the roadways, and to bike lanes and pedestrian crossing, this highly complex network safely and efficiently connects and feeds us all. Within this network, the often-unnoticed Traffic Control Systems (TCS) and Traffic Management Systems (TMS) ensure that everyday routine travel and commerce are conducted safely and, hopefully, efficiently.
“Traffic management systems (TMSs) aim to reduce traffic congestion and its related problems. To this end, TMSs are composed of a set of applications and management tools to integrate communication, sensing and processing technologies.”[1] Traditionally, traffic engineers have used a combination of two approaches: passive and active. As the traffic design, management systems, technology and the discipline have evolved, the integration of intelligent traffic control and management has occurred. This evolution has opened up the field of traffic management to a vastly larger number of potential cyber threats and vulnerabilities.
Passive, Active, and Intelligence Traffic Control Systems and Traffic Management Systems
Traffic management has never been a static discipline, for it has continually adapted to societal changes. Today, the changes seem to be constant.
The discipline has moved from passive to active systems and is beginning to transition into intelligence systems. From colonial times until recently, roadway toll lanes were initially set amounts in static locations. Stop signs and pre-programmed signal lights helped the industry evolve. These were relatively passive.
The introduction of E-ZPass and roadway weight sensors for commercial trucking began the adoption of more active measures. With roadway sensors, dynamic toll pricing, and a wide variety of other devices and techniques, the industry is moving toward, what is termed, Intelligent Traffic Management.
Passive Traffic Control Systems and Traffic Control Management
Passive Traffic Control Systems (TCS) includes the design of the roadways, the laws that govern them and the devices. A passive roadway design approach assumes, and strives to account for, the worst-case scenario, both in terms of user behavior and traffic congestion. For many years, roadways have been designed with a “passive” approach, allowing drivers to travel unpredictably at high speeds.[2]
“Passive devices provide static messages of warning, guidance, and, in some instances, mandatory action for the driver. Passive traffic control devices identify and direct attention to the location of a highway-rail grade crossing. Passive traffic control devices consist of regulatory signs, warning signs, guide signs, and supplemental pavement markings”[3]
In a passive state, a controller maintains functionality in the absence of connectivity to the rest of the traffic control network. The functionality may be directing traffic as programmed, providing local responses to emergency services and public transportation, or remaining in flash operations in case of emergency.
Within a passive state, a light can function without data collection and or monitoring status. If any traffic light is dark (without power and not flashing), the intersection impacted must begin “all-way stop” operations until local law enforcement is present and the signal is operational.[4] Circumvention of these routine controls can easily lead to public endangerment.
Active Traffic Management Systems and Traffic Control Systems
“Active Traffic Management is the ability to manage recurrent dynamically, and non-recurrent congestion based on prevailing and predicted traffic conditions.”[5] Active Traffic Control Systems (TCS) include Adaptive Ramp Metering, Adaptive Traffic Controls, reversible lanes, and traffic control software that can adjust traffic patterns in real-time.
Intelligent Traffic Control Systems and Traffic Management Systems (Intelligent Transportation Systems)
The introduction and integration of sensors and IoT devices, under the title of smart mobility, fostered a maturation towards an Intelligent Traffic Control Systems (TCS)/Traffic Management Systems (TMS) infrastructure. Intelligent Transportation Systems (ITS) is the much closer integration amongst all of the traffic management components: pedestrians, bikes, drivers, automobiles, buses, public transportation, and the traffic management system.
This integration allows for autonomous vehicles, adaptive traffic, and efficient roadway travel. ITS grants a way of sensing, analyzing, and communicating amongst the technologies intended to improve commuter and pedestrian safety, mobility, and efficiency. It utilizes adaptive signal systems, driver advisory and route planning and automated vehicles to increase the efficiency of the overall system.
With the integration of the advanced traffic controller and other external components, emergency and public transportation services have benefitted from its use. For instance, a public bus can extend the green light time, allowing for additional bus clearance called Transit Signal Priority. Transit Signal Priority (TSP) uses a location-based wireless communication method that sends a signal to the traffic controller to process changes to a movement phase. These systems are designed to remove congestion and increase traffic flow, resulting in a reduction of travel times and likely reduce the carbon footprint. For example, a preferred vehicle, i.e., public safety vehicles or public transportation, may be located and identified on the road. With that identification, the corresponding traffic controllers could be changed to prioritize the bus route.
Many of these services also reduce cost for infrastructure expenditure. For example, the City of Tampa reduces on-call signal technician hours significantly since the installation of their active traffic management software or the establishment of the E-ZPass system that automates payment services for express highways.
Protecting Intelligent Transportation Systems
How important is a roadway sign that notifies motorists that construction is present? How can an ambulance be denied their preemption on the way to save a life? Intelligent Transportation Systems (ITS) are considered the most vulnerable of all operational technologies. A mid-size municipality is likely to have thousands of roadway devices that are not protected nor monitored.
Intelligent Transportation Systems focuses on the monitoring and management of physical components and events that control industrial processes. This technology requires constant human oversight and near-perfect uptime. Most systems are typically monitored and operated by Supervisory Control And Data Acquisition (SCADA) systems. Some critical system sectors are constantly monitored and secured at the physical level. However, the localities and industry often fail to protect these systems in traffic management devices and networks.
Traffic management operations and engineers frequently do not fully realize and address the risk of vulnerable traffic systems and processes. Municipalities must seek to increase investment improving traffic cabinet security, traffic-roadway network infrastructure and reduce cyber and physical threats to traffic control systems. In many ways, through traffic control improvements, the creation of procedures, and tasking ways bad actors can exploit the systems, Smart Mobility divisions can provide an opportunity to a more safe and secure connected traffic system infrastructure.
“Traffic systems no longer have isolated network typologies, and the threats arrive faster than the scheduled maintenance periods.”
In the past, scheduled maintenance operations provided a sense of safety and compliance of all operation technologies as the maintenance periods allowed engineers a time to review and revise the implemented policies and technologies. However, in the connected age of infrastructure and the establishment of smart cities, cyber threats are more prevalent. Traffic systems no longer have isolated network typologies, and the threats arrive faster than the scheduled maintenance periods. As cars gain the ability to talk to the infrastructure, the implementation of wireless transmission and other traffic control components, Traffic Management operations, and cyber analysts must support the security and design of Traffic Systems networks.
As smart cities emerge, traffic systems become even more crucial. There will be more need for traffic control safety, integrity, and reliability. The primary goal of traffic engineering is to provide a safe, efficient, and convenient way of movement of persons and goods. To consistently achieve this goal, the standards of traffic systems design must evolve. As technology continues to integrate into traffic systems, new secure interactions between systems must ensure that the systems are designed to withhold its fail-safe mechanisms in the face of an attack.
Traffic Safety First Design Principle
For a traffic signal to be a danger to public safety, the hacker must be physically at the traffic signal cabinet. A traffic signal cabinet has a controller that is considered the brains of the traffic signal. The controller is usually the device that connects to the OT network infrastructure. A traffic signal controller can be subject to exploitation. Still, the risk of public endangerment is considerably low due to the traffic signal possessing a conflict monitor known as a Malfunction Management Unit (MMU) separate from the traffic controller. If programmed correctly, the traffic signal controller should not create a conflict in the MMU and the functions it has embedded in it.
Safety components of a control system infrastructure must be monitored and logged accurately. Data provided by monitoring and logging the system state, trends, and actions can involve parties to make predictions, investigate system issues and establish needed action.
This acquired data is utilized in the active traffic management system and supports department decisions. When traffic engineers introduced the adaptive traffic system, it can only be effective by relying on factual data for the AI system to adjust traffic patterns, provide analysis and check for anomalies. If an attacker is in the system log for an amount of time, the data it collects could affect traffic commute times, research data, and possible funding for the infrastructure.
With the inclusion of connected/autonomous vehicles Road Side Unit (RSU) and Onboard Units (OBU), many vehicles will have access to external communications, including the infrastructure. According to the threat model conducted during a 2017 study using falsified data, there are four possible traffic control attack surfaces: traffic signal controllers, OBU, RSU, and vehicle detectors. Based on the attacks, the article identified direct and indirect attacks. Indirect attacks are more likely to be conducted.[6] With many wireless technologies exposures, the impact could likely impact falsifying data, slowing network performance, and maximizing system delay. In an urban transportation system, a falsified data attack can enable a vehicle detector to activate when a vehicle is not present or move the detection zone to prevent the traffic phase from being activated if a vehicle is there. Of course, this will cause significant traffic delays, which could cause commuters to make risky traffic decisions.
An indirect attack on vehicles could also allow attackers to disable vehicle safety features in the surrounding smart mobility infrastructure. The attacker could spoof the OBU within the infrastructure to act as if a pedestrian is not crossing the street by disabling sensors or MAC addresses of phones. These categorized attacks could cause severe injuries and present bad publicity setting the autonomous vehicle program back.
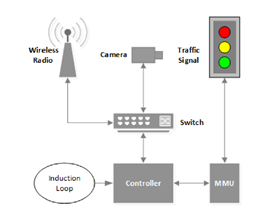
Figure 1 [7] below, shows the standard layout of a Traffic Light Intersection. Wireless radio represents the Traffic Management center’s connection, which could be fiber, copper, or other communication methods. The traffic controller directly connects to the Switch, and the MMU connects to the Controller
With an MMU, there is a smart monitor card. This smart monitor card is intended to guarantee that no phases can conflict with another unless soldered physically by a technician. For example, if the traffic signal controller is hacked and taken over, the MMU makes sure that the controller prevents any violation of the traffic signal and places the traffic signal into a malfunctioning flash.
Although it may not directly impact public safety, a failure of a control system or a Denial-of-Service (DoS) could cause issues. If a breach or attack denies the ability of these services to utilize the traffic systems efficiently, these services could create great misfortune.
What is the Risk? Potential Cyber Threats and Vulnerabilities
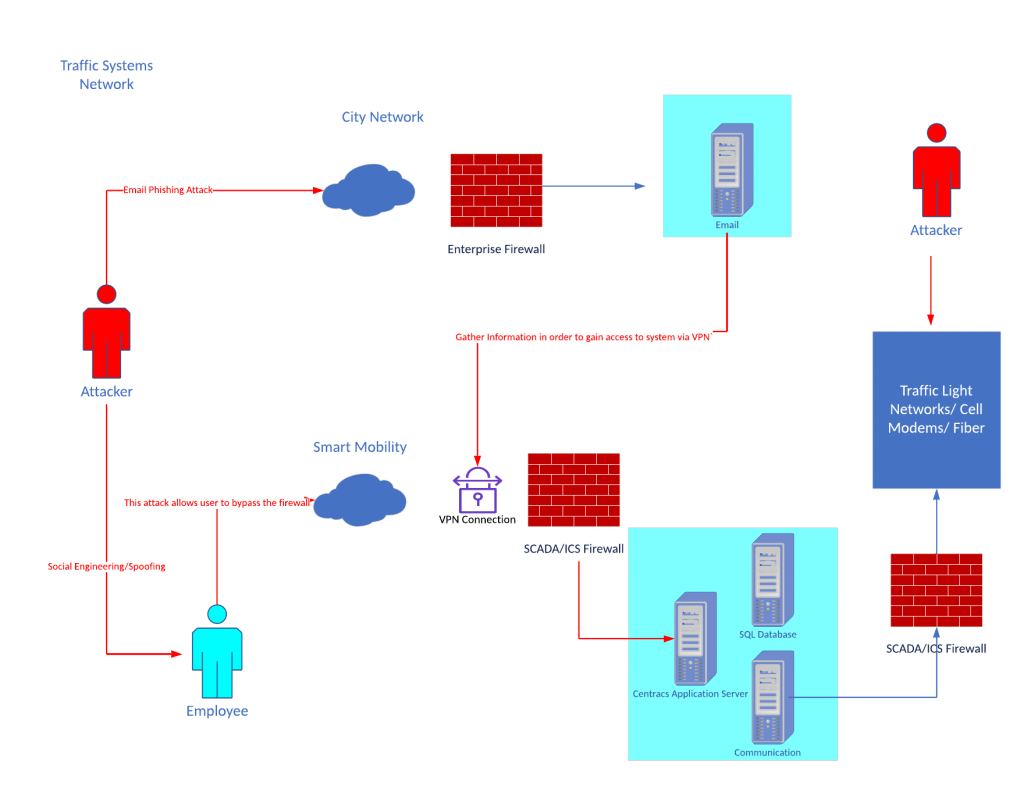
Given the complexity of the environment, the modern ITS is subject to a wide variety of potential cyber threats and vulnerabilities. A traffic control system could have thousands of weak, exposed, and unmanaged entry points within the network. In most cases, a single lock protects most traffic control cabinets. Once the adversary accesses the cabinet, many advanced traffic signals have multiple entry points that can access the network in question. Also, the attacker can infiltrate the city network by utilizing traditional methods such as social engineering, phishing, and replay attacks. Figure 2 below, entitled Notional TCS Cyber Attack Diagram, shows the many entry points within the network in a typical TCS network.
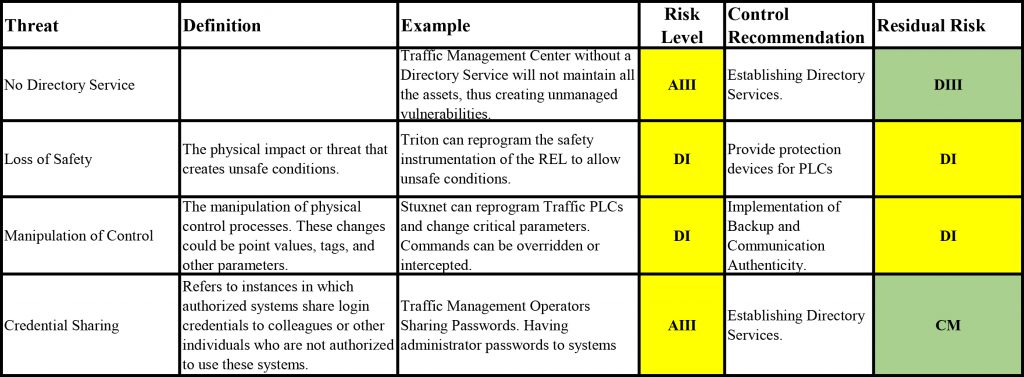
In Figure 3 below, the Notional TMS Risk Matrix chart provided includes a predefined inherent risk level that represents the amount of risk that traffic management systems have absent of controls, and a predefined residual risk that remains once controls are implemented.
Current Impediments
Although the ITS process separates each critical task, the use of connected technologies makes it an infrastructure vulnerable to many attacks prevalent within the information technology environment. Currently, an attack on ITS systems does not have a high impact on the infrastructure because it prevents safety systems from being integrated with other traffic control processes. Many of these systems and components are considered add-ons to traffic intersections. Today, attacks on ITS systems would be more of a nuisance to the public and to the traffic management centers.
Tomorrow is different. As advanced traffic systems introduce additional sensors and devices, and as connected/autonomous vehicles become more ubiquitous, cyber-attack attempts will be more likely to occur. Within the connected vehicle infrastructure, traffic signal networks interact with vehicles and cellular devices utilizing MAC addresses and other communication technologies. As threats become bold and devices become more integrated into TCS, the industry rightly fears for the public’s safety.
Lack of Trained Resources
Traffic Management Systems (TMS) are in a vulnerable state regarding personnel, the lack of resources, and support within the industry. According to Deloitte, only 124 degrees concentrating in Transportation and Highway Engineering were awarded in 2019[8]. With the job growth rate estimated to be approximately 6% between 2020 and 2028, most municipalities will lack traffic management centers and will have to rely on contractors or devices to provide services for managing traffic, road and highway designs, and other services related to traffic and roadway transportation. With very few traffic engineers, technicians, and other professionals to support the industry, the ability to address the vulnerabilities of current traffic control systems will be shelved until other obstacles are addressed.
There are many available resources for the IT industry that is not present in Operational Technology (OT), especially traffic engineering. Labor cost for traffic management and engineering is continuously rising while the appropriate skills are in shortage. The traffic engineering personnel shortage is not limited to those who maintain the system but include engineers, technicians, and project managers within the field. Most localities neglect the need for the environment because they believe IT can address the concerns of the OT traffic management networks.
“Ad hoc” Device Integration
With the implementation of the various devices, integration is not very easy. Reminiscent of information technology prior to the widespread adoption of USB ports, the implementation and integration of the IoT/OT device secured within the networked transportation environment requires specific, at times unique, skills. Although OT has made progress in data, storage processing, and communications, the proprietary advancement has been challenging to scale across multiple systems and providers. Thus, when developing technology skills in a particular control system, it may not translate to other systems that may perform the same task. Therefore, it creates a vast gap in the ability to advance personnel. Currently, many organizations are integrating OT and IT systems to reduce cost and reduce the development cycle. According to the SANS IT-OT convergence statement, the industry has significant hurdles to overcome in the pursuit of seamless integration and meeting standards to achieve high-security standards and interoperability without disrupting critical services or diverting excessive capital.[9]
The Siemens Conundrum
As the industry integrates more technologies, devices such as the Siemens RSU, begins to do more than one process. Due to the widespread adoption of Siemen’s technology, many of the company’s products and solutions developed are considered multi-vendor compatible and use port 102 to communicate.
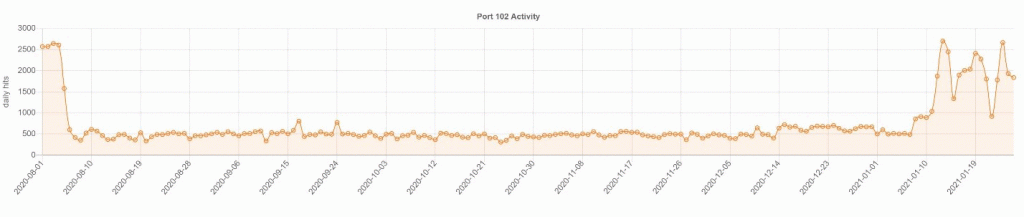
Figure 4 [10] above, is a SHODAN analysis representing attacks on Port 102 from August 2020 to January 2021. A Sentient Hyper-Optimized Data Access Network (SHODAN) is a search engine that maps and gathers information about internet-connected devices and systems. In the SHODAN analysis, the Siemens SIMTACS utilizing port 102 is constantly undergoing attacks. A successful attack on port 102 would allow the remote attacker to establish a man-in-the-middle that allows the attacker to alter, relay and monitor information of a Siemens PLC. Also, an adversary can breach the HMI control panel device and commence a denial-of-service attack that overextends resources on the network and eventually bypass the replay protection and utilize TCP protocol.
Traffic Control Systems Software
Traffic management software vulnerabilities play a role in the vendor selection and the municipality that is using it. In contrast to consumer-based applications, most control system software lacks development properties. Traffic Control Systems (TCS) software may only work with specific versions of operating systems. Within traffic management, the operating system cannot receive a build upgrade due to operations fear of loss of availability. Because of the high availability needed, it can result in the severity of the risk for a long time. Many of Siemens Control systems present vulnerabilities. For instance, Siemens AG software that manages urban traffic control systems is subjected to Cross-site Scripting. Hence, the XSS could allow the attacker to exploit vulnerabilities associated with it. Although Econolite Centracs is more secure and designed to protect from outside threats, the Centracs software has very few checks and balances. At times, a user can place an intersection in flash without command verification, or cause a light to be placed on green permanently for one direction without a timeout feature.
Going Forward: What Steps Can the Traffic Engineering Community Take?
As the traffic engineering discipline continues to evolve and adapt to the changing needs of the localities, what steps can it take to ensure the safety and security of the environment?
Adopt Standard Design Principles
One of the most difficult challenges is that technology security professionals must understand offline network IT systems do not equate to loss of functionality. Although active TMS control and monitor the state of traffic intersections, they should not impede on its safety and the availability of the system.
Similar architecture types will force the industry of Smart Mobility and ITS technology to ask questions such as:
- What ports will the system need to use?
- How are these ports monitored and managed within the operational environment?
- What data is needed for the component to function correctly?
- Does the TMS require consistent changes to traffic signals?
- Will this component be cloud/web-based?
- What is the overall risk of where this component will reside in the network?
Traffic engineering departments that are adopting ITS must continue to avoid using ITS components that can manipulate the safety program of a controller timing data, MMU, or any other data that engineers have implemented. When integrating intelligent traffic technologies, engineers must seek use cases, impacts, and studies. IoT devices that manipulate timing data of the traffic intersection could endanger motorists, cyclists, and pedestrians.
The establishment of a zero-trust architecture can be beneficial for a traffic management environment. The zero-trust architecture enables the traffic management department to establish and maintain assets connected to the network. As the ITS market grows, the ability to maintain the security of the core systems is imperative. Although the systems and enterprise architecture are tedious to implement and requires much groundwork, it allows for significant asset control management once established.
Use Standard Evaluation Frameworks
With the creation of the ICS MITRE ATT&CK® matrix, IT/OT security professionals may consider threats to traffic management systems and establish a framework to identify current attack techniques and threats to potentially provide solutions. The framework is an overview of techniques that adversaries may use within an attack. The ATT&CK for ICS is constantly updating and new methods are created along with the adoption of IT into the OT industry. The framework applies the concepts of technologies with unique characteristics in OT that considers the availability and safety of control systems. Dreamlab has provided an entry level understanding of the ATT&CK for Industrial Control Systems: Understanding ATT&CK for Industrial Control Systems (Part I).
Engineering the Future of Traffic
Concept References
Crane, C. (2021, February). Hacker Breaches Florida Water Treatment Plant, Adds Lye to City’s Water Supply. Retrieved from Security Boulevard: https://securityboulevard.com/2021/02/hacker-breaches-florida-water-treatment-plant-adds-lye-to-citys-water-supply/
Jibilan, I., & Canales, K. (2021, April). The US is readying sanctions against Russia over the SolarWinds cyber attack. Here’s a simple explanation of how the massive hack happened and why it’s such a big deal. Retrieved from Insider: https://www.businessinsider.com/solarwinds-hack-explained-government-agencies-cyber-security-2020-12
KnowBe4. (2020). The 2020 What Keeps You up at Night Report. KnowBe4. London: KnowBe4. Retrieved March 2021, from https://www.knowbe4.com/hubfs/WhatKeepsYouUpatNight-UK.pdf
References
[1] de Souza AM, Brennand CA, Yokoyama RS, Donato EA, Madeira ER, Villas LA. Traffic management systems: A classification, review, challenges, and future perspectives. International Journal of Distributed Sensor Networks. April 2017. doi:10.1177/1550147716683612
[2] National Association of City Transportation Official. (2013, September). Urban Street Design Guide: Passive VS. Proactive Design. Urban Street Design Guide 2013. Retrieved May 2021, from National Association of City Transportation Officials: https://nacto.org/publication/urban-street-design-guide/design-controls/
[3] Law Insider. (n.d.). Passive traffic control devices definition. Retrieved from Law Insider: https://www.lawinsider.com/dictionary/passive-traffic-control-devices
[4] Department of Transportation. (2021). Manual on Uniform Traffic Control Devices for Streets and Highways, 2021. Retrieved from Federal Highway Administration: https://mutcd.fhwa.dot.gov/
[5] Department of Transportation. (2021). Manual on Uniform Traffic Control Devices for Streets and Highways, 2021. Retrieved from Federal Highway Administration: https://mutcd.fhwa.dot.gov/
[6] Feng, Y., Huang, S., Chen, Q., Lui, H., & Mao, Z. (2018). VULNERABILITY OF TRAFFIC CONTROL SYSTEM UNDER CYBERATTACKS USING FALSIFIED DATA. The Journal of the Transportation Research Board. Retrieved February 2021, from https://www.ics.uci.edu/~alfchen/yiheng_trb18.pdf
[7] Ghena, B., Beyer, W., Hillaker, A., Pevarnek, J., & Halderman, J. A. (2014). Green Lights Forever: Analyzing the Security of Traffic Infrastructure. USENIX Workshop on Offensive Technologies. 8th, p. 2. San Diego, CA: University of Michigan Engineering and Computer Science Department. Retrieved from https://jhalderm.com/pub/papers/traffic-woot14.pdf
[8] Deloitte. (2019). Data USA. Retrieved from Deloitte: https://datausa.io/profile/cip/transportation-highway-engineering
[9] Gregory-Brown, B., & Harp, D. (2016). Security in a Converging IT/OT World. SANS. A SANS Whitepaper. Retrieved March 2021, from https://www.ge.com/fr/sites/www.ge.com.fr/files/SANS-wurldtech-whitepaper-Security-in-IT-OT-Nov-2016.pdf


Leave a Comment