A data breach can hit any business at any time. Whether it is sensitive information that the company must protect to maintain its competitive advantage or documents necessary to meet industrial or government’s regulatory requirements, all data must be protected. The fallout of a data breach has a significant impact on any business.
Data breaches may include the theft of intellectual property, disclosure of personal identifiable customer information, theft of financial information about customers, health data, etc. Between January 1, 2005 and April 18, 2018, there have been 8,854 recorded breaches in which approximately 7.89 billion records were compromised. Many of these records were on disks, hard disks, removable storage devices, mobile devices, and other locations storing unstructured data.
No industry or business is safe from cyber threats and security breaches that happen around us every day. Data breaches require public disclosure for customers, partners, suppliers, shareholders and government agencies.
Crunch the Numbers
The cost of corporate data breaches are high and becoming increasingly important. Research led by Cisco indicates that 31% of organizations in the world have experienced a cyber attack on their operational technology infrastructure. Moreover, the average cost of an attack, according to estimates by Accenture, is $2.4 million.
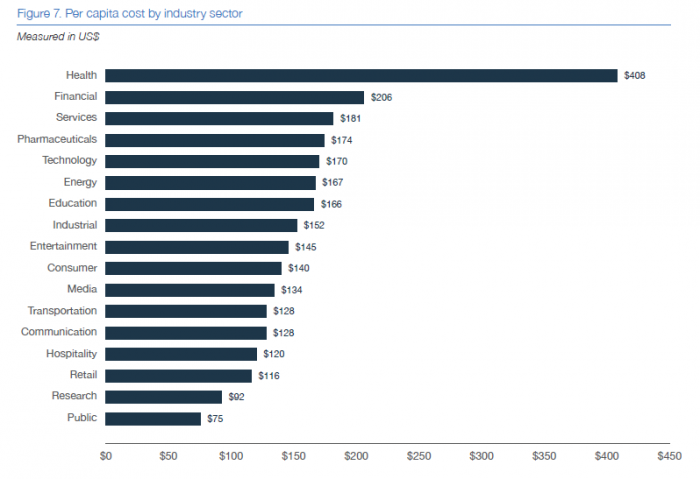
These costs depend on many factors, including the size, the costs of detecting and escalating the violation. Additionally, post-incident costs of the breach such as technical assistance, corrective measures, legal fees, identity and credit protection services affect these costs. The numbers are also much higher for violations that occur in the regulated sectors. For example, a health data breach can cost an average of $408 per record.
A data breach also affects a company (with costs incurred by ransomware damages expected to go above $8 billion) and causes a loss of customers. Additionally, these breaches damage a brand’s image and reputation. This all conspires to negatively affect the company’s end results.
The volume of data breaches and the recent high-profile violations show how cybersecurity is challenge. Indeed, a breach can be truly difficult to avoid, even for the best-intentioned companies.
THE MOST COMMON CYBER ATTACKS
There is no doubt that the consequences of cyber-attacks are disastrous for any organization. These attacks explore new ways to damage companies and take their data hostage. For this reason, it is vital to be clear about the most common types of basic cyber attacks and what they can do to a business.
Spyware
The purpose of this malware is to infect computers to collect information contained in it. Once it is in possession of data, it transmits the information to an external entity without the owner’s knowledge or consent. Numerous hackers use it to profit from the sale of sensitive information. The large amounts of data that companies generate daily is a goldmine for this harmful virus.
Phishing
Another dangerous attack that companies frequently face is phishing. This type of cyber-attack expands via e-mail, which makes the transmission very fast. Again, information theft is the main purpose of cyber-criminals. How do they access required data from specific people or companies? Through infected emails. According to data, ransomware from phishing emails increased 109% over 2017.
Adware
This software displays ads that aim to steal data from users. These ads obtain user information by often redirecting users to websites that wish to collect data. Additionally, these ads can automatically download content onto your laptop or phone.
Ransomware
The frequency of ransomware attacks are increasing with every passing year. These attacks block the system of a company or institution, requesting a ransom in exchange for access to their own data and systems. The effects can be catastrophic, because the company in question is totally paralyzed.
Large companies have suffered attacks of this type recently, generating a considerable media stir. However, ransomware viruses, which are increasingly sophisticated and focused on mobile devices, have become much more visible in society.
Worms
Along with Trojans, worms are one of the most common internet attacks. Their method of action is simple: they transmit information by replying, sending copies to other teams, and promoting a quick and dangerous extension. The first computer worm in history, the Morris worm, dates back to 1988. Since then the formula has continued down the path of perfection to attack all types of equipment.
NEW THREATS
Betting on digital transformation is a necessary challenge that companies are gradually assuming. Framed in it is cybersecurity, an aspect that must be taken care of to avoid unpleasant and harmful situations for the organization. The reality is that hazards present themselves in a more sophisticated and incisive way, so precautions must be taken to greater extent.
Hackers use network devices, which are common use in companies. For example, the printer already has access to the internet. Therefore, it is likely that the printer will be very vulnerable when it comes to spreading the virus.
However, the truth is that the printer is not the only device with virtually no security. There are other devices that end up infected and damaged by cyber-attacks while they are connected to the internet. Examples include employee’s smartphones, the refrigerator, and the router itself.
Finally, another very widespread technique is the use of drones. In this case, the consequence is much more practical and direct. Drones enter private spaces of companies and institutions, record and obtain data without consent and, in many cases, sell them on the black market.
How to Deal with a Data Breach?
Good security practices and compliance with cybersecurity frameworks can help you. But whichever approach you decide to use as the basis of your security efforts, keep in mind some key trends. The first is that the perimeter of the traditional network has dissipated.
Employees no longer need to work within corporate boundaries and access resources through a heavily-protected network. At the same time, attackers have become more competent at breaking down the defenses of traditional business perimeters.
Identity Management
In addition, the number of identities and the nature of identity management within the enterprise changes. Users who access sensitive resources include employees, partners, suppliers, customers, and so on. Moreover, the Internet of Things (IoT) and automated robotic processes are transforming the very notion of identity.
Identity management must be at the center of all prevention efforts against violations, to prevent current and future cyber threats from accessing sensitive data. Effective identity management helps companies enforce who should have access to which systems, applications, and data. In addition, because of the wealth of information in the access logs, effective identity management can identify how the violation occurred.
According to SailPoint’s 2018 Market Trends Survey, while the companies understand the threat posed by a data breach, they struggle to introduce a high level of visibility into their systems. Fortunately, interviewees knew that the best way to get this visibility was to manage identities. More than half of them believe that identity management is the foundation of their future security strategies. Additionally, 87% understand how robust identity management is essential to effective security.
Rather than hoping that a violation will never happen in your business, it is best to limit the risks as much as possible. Planning ahead and attempting to proactively secure as much business-sensitive data as possible before an attempted breach, while being prepared for the eventuality that it occurs, is the best way to secure the data.
Tags: Adware, Cyber Threats, Cybersecurity, data breach, Data Security, Internet of Things, IoT, Phishing, Ransomware, Worm


