For most of us, cybersecurity means network and data protection. We think of intrusion detection, firewalls, secure network design, secure and trained workforce, social engineering, and other security activities. Essentially, we view cybersecurity as the tools and activities that keep our networks and the data that they handle secured. But what if one of the components of your network has a security flaw built into it? Traditional information assurance practices don’t help if the components of the network are built to send your data to someone outside of the network or to leave a back door open for potential intruders.
In reality, many networks have been compromised by components with security flaws built into embedded software code. These flaws can be difficult to detect since they are usually masked by the proper functioning of the device. As such, the code can be considered unwanted added functionality.
Think about the networks you work with now. Do you know who built the components (keep in mind, many companies use contract manufacturers)? Are they authentic? Free from back doors or other malicious code? Can you be sure?
Understanding and managing the supply chain is an important part of your cybersecurity program. Preventing compromised components from entering your network will improve security and can also increase reliability.
Understanding the supply chain is especially important for information and communication technology (ICT) products because the extended and global nature of these supply chains make them vulnerable to counterfeit and malicious product insertion. ICT supply chains tend to have multiple organizations in multiple regions involved in the production of a product, and this complexity makes them difficult to manage. The short product life cycles typical for the ICT industry also mean that supply chains are constantly changing to take advantage of new technologies.
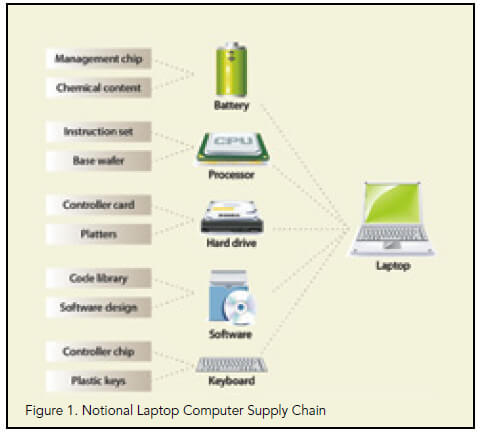
Let’s take the supply chain for a typical laptop computer as an example. We are generally aware that laptops are assembled from component parts—a processor chip made by Intel or AMD, a hard drive made by Seagate or Western Digital, etc. But do we consider that each of those components is made of sub-components from sub-tier suppliers? The hard drive has a motor to spin the drive, a controller card, cable connectors, a case, etc., which can all be produced by sub-tier suppliers. Some of these components and sub-components, such as memory chips, are commodity items that are often purchased from the lowest cost supplier. In addition, many of these items are actually manufactured by a contract manufacturer. Quickly, this supply chain can become very complicated with some unknown portions, as shown in figure 1.
When we look at the ICT supply chain from a cybersecurity perspective, we need to add yet another layer of complexity: software. While most supply chain professionals have experience managing the flow of physical items through the supply chain, cybersecurity professionals must also consider where the software came from. Who wrote it? Where is it stored? Who has access to the code along the supply chain? In many ways, the software supply chain is more of a concern than the hardware supply chain. There are ways to detect tampering with packaging or a counterfeit product. Software tampering requires code analysis to detect, a process which is time-consuming and costly, if source code is available, and even more challenging if not.
Who you buy your ICT equipment from is important, but who your suppliers buy from, and who they, in turn, buy from is equally important in understanding the risk of receiving a compromised product. ICT supply chains are extended and dynamic, so how do you start to gain some control?
Establish the system context
Start by understanding the context of your supply chain. In other words, what can the environment you operate in tell you about your cybersecurity risks. The context consists of the product’s use, what it is connected to, and who the users are. Keep in mind that this context will likely be different for every system and potentially for individual components.
Start with how the product will be used. Here, the focus is on what type of data will be managed in the system. Essentially, you need to determine the consequence of the data being compromised or leaked outside of the system. While any system breach is bad, the compromise of a system managing classified data is a much higher risk than a system that is managing publically available data. Understanding the use of the ICT equipment will help determine the resources appropriate to secure the system. In reviewing the product use, consider what other systems are connected to the focus system. A less secure system can serve as a pathway to attack a more highly secured connected system. This was the method used to steal credit card numbers from Target in 2013.
Another consideration is how the system is connected to the rest of the world. A system that is connected to the public internet will need more reliable security, since it would be easy to find and attack. On the other hand, a system that is isolated from any other network would have a much lower risk of attack or data breach, since the attacker would need to be in physical proximity of the system.
Finally, consider who the system users are. Are the users internal employees who are trained on security procedures, or is the system accessed by a public user base which may not consider risky security behaviors? Simple security procedures, such as keeping passwords secret and maintaining current anti-virus software, cannot be counted on if you do not directly control the users’ environment.
Taking these three elements into consideration will provide some context on the risk and impact of a compromising event. This context will, in turn, help establish the level of risk management activity you need to employ when managing the supply chain. The more valuable the data managed and more connected the system is, the more resources should be applied to ensure that the ICT components of the system are authentic and free of malicious code.
Who you buy your ICT equipment from is important, but who your suppliers buy from, and who they, in turn, buy from is equally important in understanding the risk of receiving a compromised product.
Understand your procurement
The supply chain for a product and the risk of receiving a compromised or counterfeit product is dependent on the type of product you are evaluating. Consider how the product is made and sold to understand where it is at risk.
For example, a commercial off-the-shelf (COTS) item, especially a commodity, is likely to have a supply chain designed for efficiency and cost savings. Consider laptop computers, which are in a very cost competitive market with essentially commodity components. This means that the supply chain will likely include multiple organizations located in low-wage countries, which, in turn, means multiple points where counterfeit or compromised components can be inserted into the supply chain. In short, for many COTS ICT products, supply chain visibility and sub-tier management is difficult.
Customized products, on the other hand, tend to be made with specialized sub-components that are driven by the unique requirements of the product. In this case, the supply chain is typically well known and there may be direct communication with sub-tier organizations. Consider the Apple iPhone supply chain, where Apple directly manages sub-component suppliers from design through assembly. Although this supply chain reduces the number of entry points for tampering, it may be easier for an adversary to target specific suppliers.
Of course, these are just general guidelines for understanding what visibility you might expect in the supply chain. Some COTS product manufacturers maintain good visibility over their supply chain and manage their risk well. At the same time, some customized products can be built with multiple COTS components, making the supply chain opaque.
As important as the type of product you are purchasing is how you purchase it. Open procurement, which often focuses on providing the lowest cost solution that meets technical requirements, can be higher risk than working with a trusted sole source provider. Using distributors or other intermediaries can obscure the actual supply chain and raise the risk of receiving an unauthorized item.
Another key consideration is how your suppliers purchase their components and how sub-tier suppliers perform their purchasing functions. Since ICT supply chains rely so heavily on component suppliers, the procurement practices of every participant in the supply chain can have a profound impact on the risk of a compromised product entering the supply chain.
Taking action
So now that you better understand the cybersecurity risks in your supply chain, what can you do about it? While every supply chain and situation is unique, there are some general steps you can take to reduce your risk exposure and provide a more secure system.
The first step is to map your supply chain and identify where you have cybersecurity risk exposure. Laying out the players in the supply chain and where they are located will help you understand the scope and complexity of the supply chain. Including geographic locations will also help you decide if the location of certain suppliers presents any risk to your organization. When mapping the supply chain, keep in mind that you want to map the actual manufacturing locations for the components, and, in some cases, this may mean that you need to identify the contract manufacturer. Also, some items may be produced in multiple locations.
In most cases, you will find parts of your supply chain where you do not know who is involved or how the items are handled. Here, you need to consider what effort is required to be able to map that portion of the supply chain and the value that additional information will provide to your analysis. Obtaining that additional information may not be worth the expense, and you may be better off accepting the increased risk in that portion of the supply chain and taking actions to mitigate that risk.
Once you have the supply chain mapped, you can identify the areas where there is a risk of counterfeit or compromised items entering the supply chain. To identify risk areas, look for:
- locations in geographic areas known for counterfeit production or hacking activity;
- locations or transportation routes with inadequate physical, information, or personnel security;
- locations with inadequate procurement processes or known purchases from gray market suppliers; and
- products that use insufficiently tested software code or with outdated code.
Also, include risk considerations unique to your system and your operations. In identifying cyber security risks, your focus should be on the locations that produce or handle information or software bearing components. That is, those components that will carry some sort of data or software code. In other words, we are not worried about the plastic case, we are concerned with the various processors and other electronics components.
The first step is to map your supply chain and identify where you have cybersecurity risk exposure. Laying out the players in the supply chain and where they are located will help you understand the scope and complexity of the supply chain.
With your risk exposure identified, the next step is to take action to treat the risk. By “treat” we mean to either reduce the likelihood that the risk will occur, reduce the impact if the risk does occur, transfer the risk to another party, or accept the risk and prepare a response plan. The exact approach you use will depend on your risk tolerance and the level of resources available for risk mitigation. In any case, you should include a process of prioritizing your risks to ensure you treat the highest risk exposure areas first.
Risk treatment can take many forms. We present a few examples here, but it is important to make sure your risk treatment activities fit with the products you are addressing and the capabilities of your supply chain partners. Since we are talking about taking actions in your supply chain, it is important that you coordinate your risk management actions with key suppliers. Often, you will need suppliers and other partners to take the actions needed to reduce risk. Coordination and collaboration are essential for managing cybersecurity in the supply chain.
One method of treatment is to provide better specifications for the products you buy. Specifically, more detailed specifications about the security requirements for the product as well as specification on the manufacturing conditions may be required. Better specifications can help eliminate any lower grade alternatives from the supply chain and also ensure that the product arrives with the security features you need it to have.
Another action is to focus your supplier pool by pre-qualifying suppliers that meet your risk management criteria. By focusing your suppliers, you can eliminate higher risk suppliers from the procurement and also maintain a cadre of suppliers that is a manageable size to collaborate with. This will not only reduce the potential of having to work with a high risk supplier, but also increase the probability of success for other treatment actions. In cases that require high assurance, focusing the supply base can mean working exclusively with trusted suppliers who meet exacting criteria for quality and cybersecurity. Keep in mind that there is a tradeoff to focusing the supply base in the form of reduced competition and, as a result, potentially higher prices.
You can also manage cybersecurity in the supply chain by requiring adherence to operating standards. Standards bodies, such as the Open Group (Open Trusted Technology Provider Standard [O-TTPS]), ISO (Draft ISO/IEC 27036—Information Technology—Security Techniques–Information Security for Supplier Relationships), and Software Assurance Forum for Excellence in Code (SAFECode) (Software Integrity Framework and Software Integrity Best Practices), provide standards that represent best practices for managing a secure supply chain. You should note that standards are a low-impact way of reducing risk because the practices are pre-defined. However, standards are designed to be general, and you may need to go beyond the standards practices to get the level of risk management you need.
In addition to standards, you can work with your industry to define practices for reducing cyber- security exposure across the industry sector. Industry specific standards can be useful, since they address the unique requirements and challenges of your industry. However, like other standards, they may not provide the rigor that you need. Working within your industry may also help you identify best practices that you can apply to your own supply chain.
Staying vigilant
These recommendations are general in nature, but provide a foundation for a good supply chain cybersecurity program. Remember that security requires vigilance, especially in an ICT supply chain where short product cycles mean that the supply chain is constantly changing. Your risk management practices need to keep pace with this change in order to be effective. The best way to remain vigilant is to establish a management process to continually review your supply chain risk exposure and make adjustments as changes require.
Remember that it is not only in installing a new system that you face the risk. Replacing and maintaining components need to be subject to the same requirements and scrutiny to secure your supply chains and systems.
The insertion of counterfeit products and malicious code into the supply chain is a reality. Taking actions to understand your supply chain and reduce your cybersecurity risk exposure is essential. By maintaining a secured supply chain, you can reduce the cybersecurity burden on your network operators. Many of the leading practices for supply chain cybersecurity have been documented and established in standards. Take advantage of the work already done to secure your supply chain and keep the bad guys on the outside.



Leave a Comment