Next-Generation Cybersecurity
Mobile Security Research – A Massive Waste of Time
Author(s):
Brian Robison, VP of Product Marketing & Chief Evangelist, Corellium
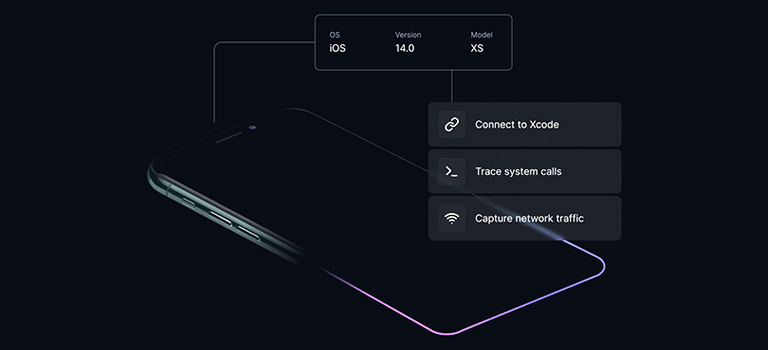
Mobile security research and testing have traditionally been extremely difficult and time-consuming endeavors. And most of that time is spent doing things other than the actual research. Whether searching for vulnerabilities in a mobile OS, penetration testing a mobile app, or conducting research into mobile threats and malware, all are bound by the restrictions imposed … Read more