Securing the Network
The Case for Moving Beyond VPNs: Embracing Conditional Access
Author(s):
Alex Haynes, CISO , IBS Software
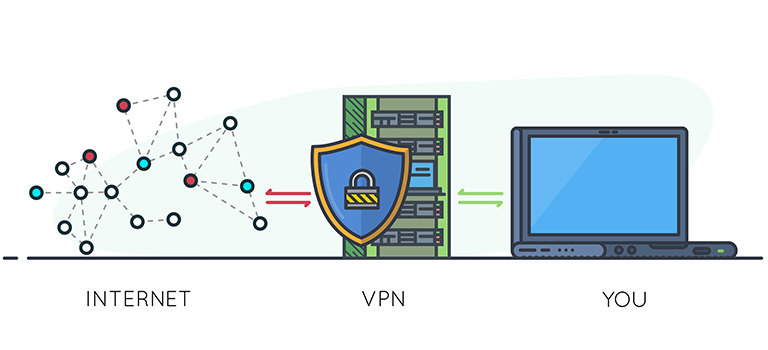
In the ever-evolving landscape of cybersecurity, traditional tools, and approaches to securing remote access, such as Virtual Private Networks (VPNs), are increasingly seen as inadequate for the complex demands of modern enterprise environments. The shift towards a more dynamic, distributed workforce, along with the proliferation of cloud services and mobile computing, necessitates a re-evaluation of … Read more