Understanding the Tech
9 Ways You Can Use Raspberry Pi to Improve Your Life
Author(s):
Rina Richell, SEO Analytics Manager,
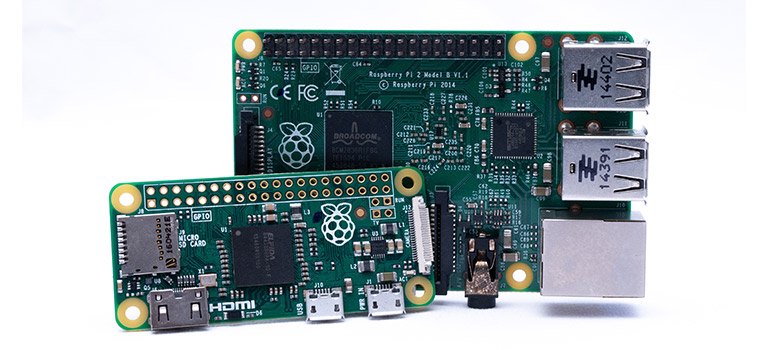
Raspberry Pi Foundation, a UK charity, created a series of single-board computers. The purpose of the innovation was to educate people in computing and make it easier for more people to access computing education. The Raspberry Pi was launched in 2012 and has rolled out several variations since then. Indeed, this innovation has moved on … Read more