The threat landscape in the cyber domain has changed. A secure perimeter comprised of traditional network security devices, technologies and mechanisms is necessary but it is no longer sufficient to defend against the threats that exist in the current environment. The proliferation of Advanced Persistent Threats (APTs) executed by sophisticated adversaries has changed the cybersecurity game. To put this in a more familiar context, traditional cyber threats are like missiles and APTs are like spies. Just as a country would not use a missile defense system to try and stop a double agent from stealing state secrets, organizations cannot rely solely on perimeter defense strategies and traditional security mechanisms to stop adversaries that are growing more sophisticated and cunning every day.
The constant evolution of threats makes security in the cyber age a daunting task. Organizations must continue to patch known vulnerabilities and defend against known threats. At the same time they must also defend against unknown threat actors exploiting unknown vulnerabilities that are increasingly difficult to detect after the network has been infiltrated.
Evidence of the evolving threat landscape is everywhere. According to Mandiant, “46% of compromised machines have no malware on them and 100% of victims have up-to-date anti-virus software.”1 The more sophisticated attacks circumvent these traditional defense strategies and target entry points that are easier to exploit without detection. The human user is more frequently becoming exposed as the weak link of choice in the cybersecurity chain. Risk attributed to the human factor is supported by a recent report published by Trend Micro where they identify that “91% of targeted attacks involve spear-phishing emails, reinforcing the belief that spear-phishing is a primary means by which APT attackers infiltrate target networks.”2 The threats are growing more sophisticated, traditional defense strategies are no longer sufficient and the most difficult element to account for – the human factor – is consistently in the cross hairs of malicious actors.
The good news is that all is not lost. While there is no silver bullet or one-size fits all approach to cybersecurity, organizations can reduce risk by employing a layered multi-dimensional approach to defend networks and mitigate damage after breaches occur.
New technologies that employ advanced methods of analysis that are able to identify and contain APTs as well as integrate with traditional security mechanisms can significantly improve the security posture of many organizations. However, technology alone does not address all cyber risk. With the human factor exposed as the glaring weakness for most organizations, meaningful cybersecurity awareness training is a quick and relatively inexpensive way to reduce risk and improve overall cybersecurity.
In order for cybersecurity Awareness training to be effective it has to change behavior of users. This means that the content must be relevant but also delivered in such a way that captures the attention of the participant without interrupting the normal flow of business. Some recent widely publicized breaches, including the RSA breach in 2011 and the Target breach in late 2013, happened because of a momentary lapse in judgment or by organizations failing to implement known best cybersecurity practices. Cybersecurity training will not eliminate poor decision making but when done effectively it can help users consider cyber implications in their normal decision making process. Based on the current threats and the number of breaches originating with a person inside the organization it is clear that the traditional practice self-directed training and checkbox quizzes to satisfy cybersecurity awareness training requirements is not the answer.
In the RSA breach a “zero-day” attack, one that exploits a previously unknown vulnerability, was launched through an email phishing campaign that tricked users to open an Excel file attached to the email. According to an article published in Wired Magazine in August of 2011, “ the attachment used a zero-day exploit targeting a vulnerability in Adobe Flash to drop another malicious file — a backdoor — onto the recipient’s desktop computer. This gave the attackers a foothold to burrow farther into the network and gain the access they needed.”3 When opened, the zero-day exploited an unknown flash vulnerability that ultimately allowed the attacker to ex-filtrate RSA proprietary data. Cybersecurity training that highlights phishing campaigns and the implications of zero-day attacks can help users better understand the consequences of falling for this type of threat. With cybersecurity at the forefront of the users mind they will be more likely to avoid suspicious emails with attachments, or at a minimum raise concerns when they receive a suspicious email so that other users can be warned.
The more recent Target breach was far less sophisticated than the RSA breach, but the results were massive. According to Brian Krebs, the security blogger credited as the first to report on the breach said that, “the initial intrusion into its systems was traced back to network credentials that were stolen from a third party vendor.”4
Krebs reports that the attacker was able to upload credit card-stealing malware onto select Target cash registers using network credentials that originally belonged to a third party HVAC company. By the end of November 2013 Krebs says that, “the intruders had pushed their malware to the majority of Target’s point-of-sale devices, and were actively collecting card records from live customer transactions.”5
Based on the information that has been reported, Target may have been able to minimize the damage or possibly avoid the breach altogether by implementing network segmentation, a practice that is highly recommended by the Payment Card Industry Security Standards Council.6 If employees responsible for granting network access to venders were trained to be aware of this best practice and, if network segmentation were employed correctly, the attacker would not have been able to use credentials stolen from a third party vendor to upload malware onto cash registers. Effective cybersecurity awareness training for all employees, including those in technical roles, can help raise awareness of best cybersecurity practices. Increased knowledge of best practices can help ensure they are followed whenever possible, or increase the likelihood of someone within the organization raising concerns when best practices are not implemented.
The cost of even one employee not having proper cybersecurity awareness training are high. To help organizations of all shapes and sizes, the CyberCenter at Anne Arundel Community College takes cybersecurity awareness training several steps further. The CyberCenter offers instructor-led interactive courses that are broken down into 90 minute modules delivered when and where it is most convenient for the organization. In addition to a delivery approach that moves at the speed of business, the CyberCenter’s meaningful interactive training helps organizations create a cybersecurity aware culture that transforms the human factor from vulnerability into asset. Technology users that are cyber aware and have the skills to recognize, avoid and mitigate damage after a breech occurs become a kind of “human based firewall” that brings cybersecurity out of the network closet and into the forethought of every user.
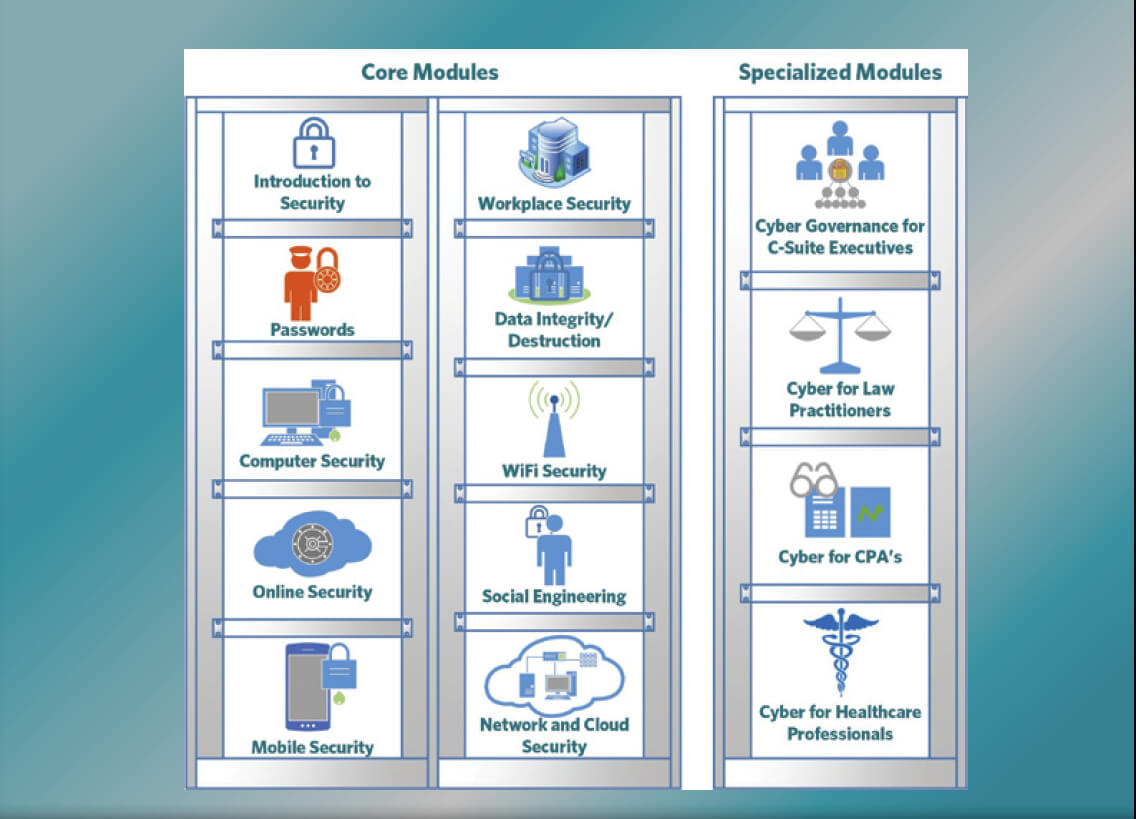
To achieve these outcomes, the CyberCenter’s approach to cybersecurity training is comprised of ten core modules and four specialized modules. The core modules address everything from passwords, to social engineering, to network and cloud security. The core modules are designed to help organizations build a cybersecurity awareness baseline across the workforce. From the corporate leadership that is often the most targeted group in an organization, to the front line employees that use technology to complete daily tasks, to the technical staff that hold the keys to the organizations most valuable data, the CyberCenter’s Cybersecurity Awareness Training applies to all personnel in the organization.
The four specialized modules that make up the CyberCenter’s baseline cybersecurity awareness package focus on training for C-Suite Executives, Law Practitioners, CPA’s and Healthcare professionals. These specialized modules are developed and delivered in collaboration with subject matter experts that have the appropriate real-world experience and education required to present contextualized training to these specific groups.
Cyber risk is everywhere and the threats will only become increasingly sophisticated and targeted. While it is not possible to both use technology and be immune to risk, taking an in-depth approach to cybersecurity that not only incorporates technology but also meaningful cybersecurity awareness training is an effective approach that organizations of all shapes and sizes can employ.
Sources
- Mandiant. (2014, 02 10). Threat Landscape Overview. Retrieved from Mandiant: https://www.mandiant.com/threat-landscape/
- TrendLabs APT Research Team. (2012). Spear-Phishing Email: Most Favored APT Attack Bait. Cupertino, CA: Trend Micro Incorporated.
- Zetter, K. (2011, August 26). Researchers Uncover RSA Phishing Attack, Hiding in Plain Sight. Retrieved from Wired: http://www.wired.com/threatlevel/2011/08/how-rsa-got-hacked/
- Krebs, B. (2014, February 05). Target Hackers Broke in Via HVAC Company. Retrieved from Krebs on Security: https://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company/
- Krebs, B. (2014, February 05). Target Hackers Broke in Via HVAC Company. Retrieved from Krebs on Security: https://krebsonsecurity.com/2014/02/target- hackers-broke-in-via-hvac-company/
- PCI Security Standards Council LLC. (2010). Payment Card Industry (PCI) Data Security Standard: Requirements and Security Assessment Procedures Version 2.0. PCI Security Standards Council LLC.


Leave a Comment