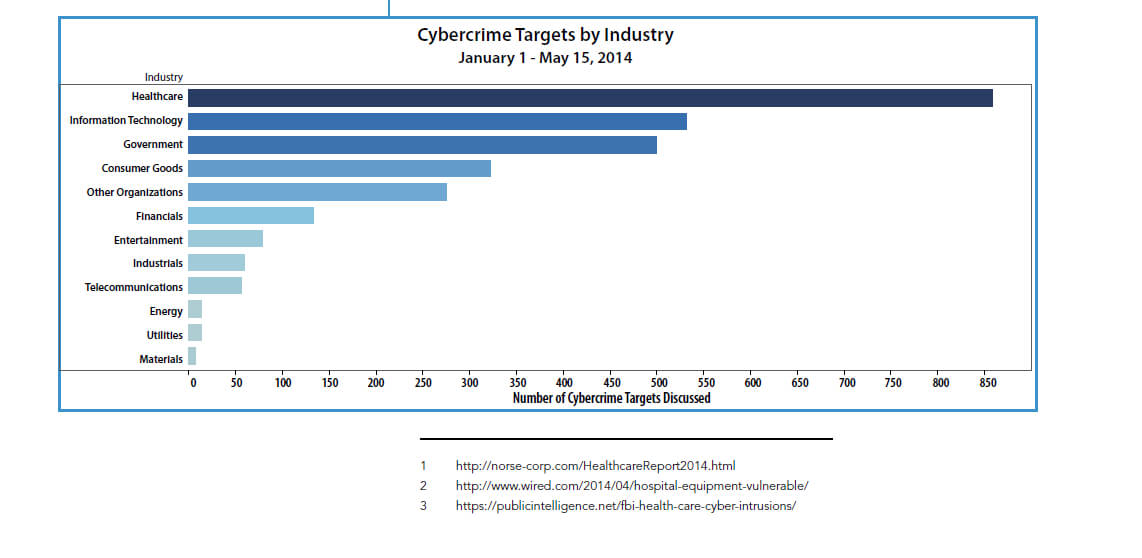
Cybersecurity & Your Business
O (Big) Brother, Where Art Thou?
Author(s):
Jim Mazotas, Founder, OnGuard Systems LLC
Larry Letow, CEO, U.S., CyberCX
“…For the traitor appears not a traitor; he speaks in accents familiar to his victims, and he wears their face and their arguments, he appeals to the baseness that lies deep in the hearts of all men. He rots the soul of a nation, he works secretly and unknown in the night to undermine the … Read more