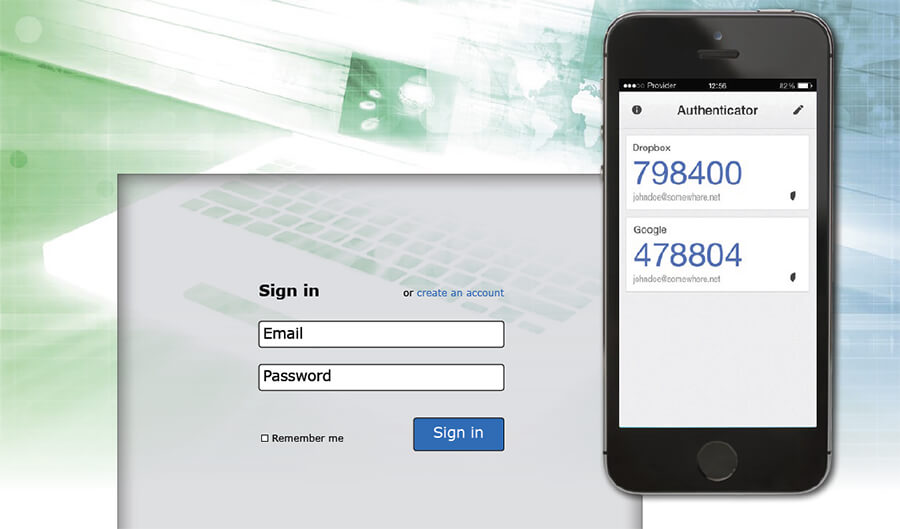
Cybersecurity & Your Business
Why Your Business Should Use Two-Factor Authentication
Author(s):
Greg Gunther, Software Engineer, Visionist, Inc.
A 2011 study by University of Cambridge computer security researcher Joseph Bonneau uncovered a shocking reality. Bonneau compared two password databases leaked from popular websites (Gawker and rootkit.com.) He discovered that over 31% of users who had an account on both sites reused the same password1. Equally troubling is the recent news that a Russian … Read more