New survey findings suggest remote work and security still not mutually inclusive
Multiple surveys on employee efficiency, happiness, and health have been conducted since the pandemic began in the Spring of 2020. Most have reached the same conclusions – a more flexible schedule, a more comfortable work environment, and the removal of the daily commute can result in reduced stress and improved productivity. Many organizations have extended their telework policy or are employing a hybrid model, which is likely to continue moving forward.
However, to make all of those benefits possible, and to simply sustain business operations and meet mission objectives, agencies across federal, state, and local governments have been forced to alter the way their employees work – how they access job-critical tools and applications, and how they access and share data. Yet, despite such tangible benefits for government employees, has agency security also benefited from the change?
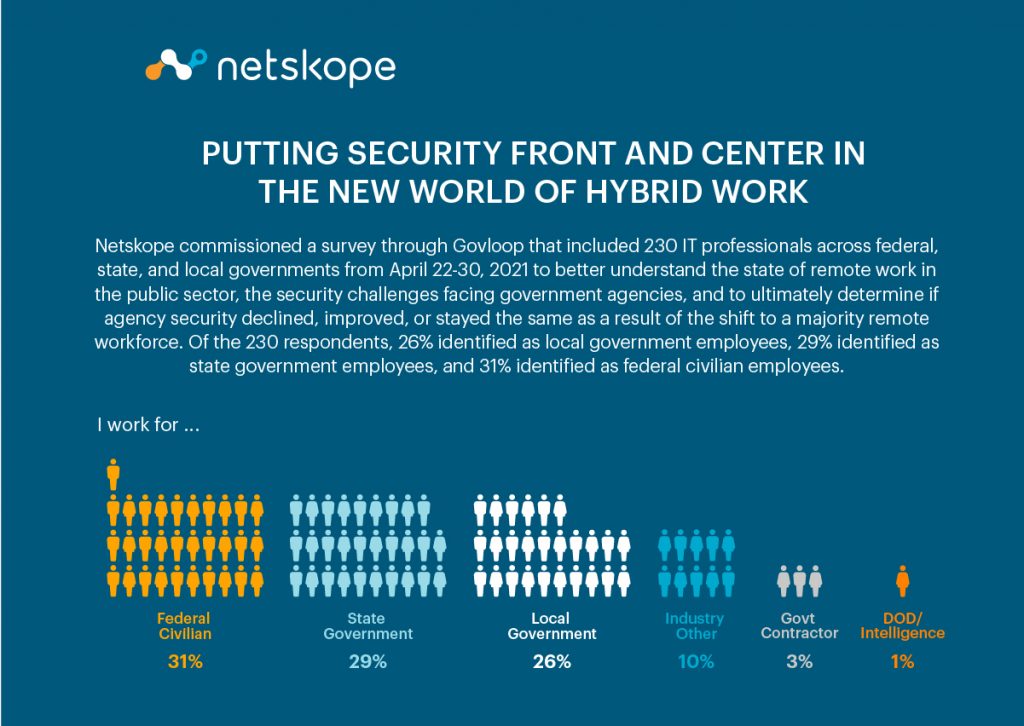
Netskope commissioned a survey through Govloop that included 230 IT professionals across federal, state, and local governments from April 22-30, 2021 to better understand the state of remote work in the public sector, the security challenges facing government agencies, and to ultimately determine if agency security declined, improved, or stayed the same as a result of the shift to a majority remote workforce. Of the 230 respondents, 26% identified as local government employees, 29% identified as state government employees, and 31% identified as federal civilian employees.
Agency Overreliance on Virtual Private Networks (VPNs)
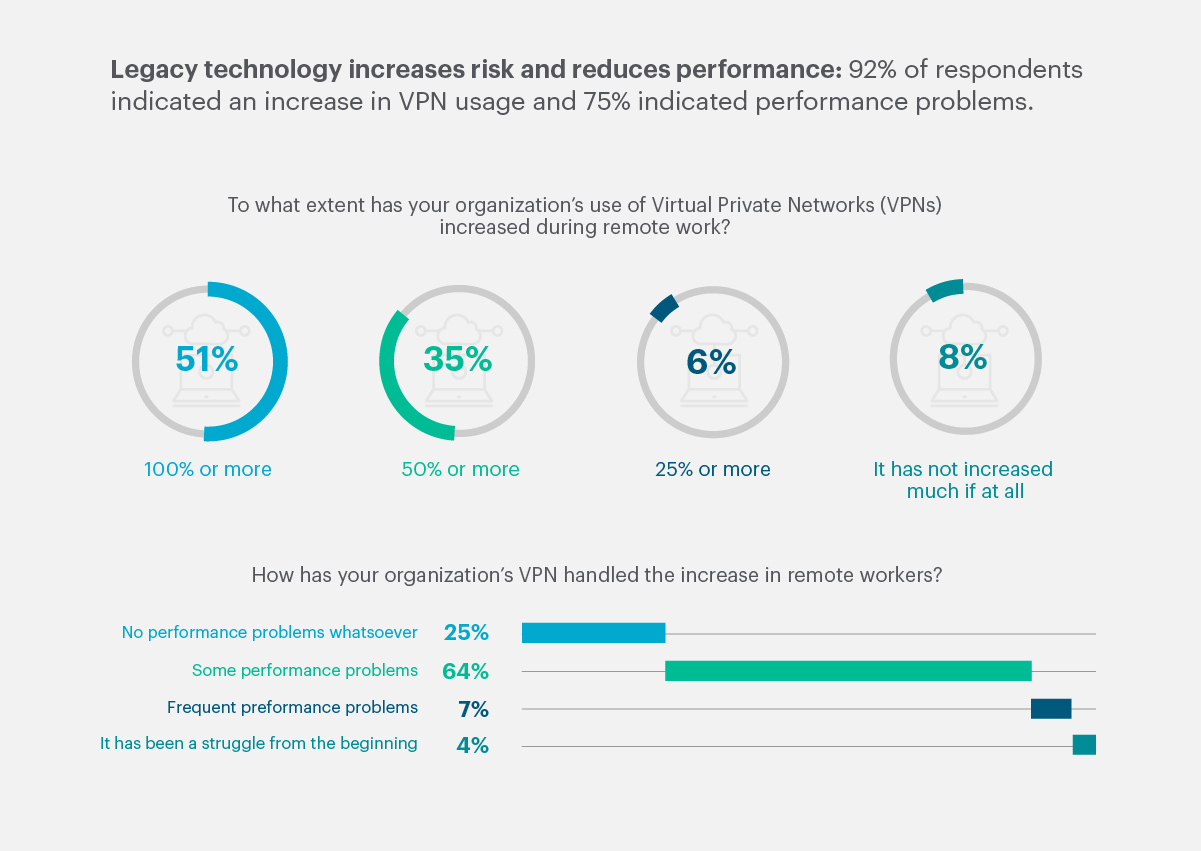
Government organizations faced a unique challenge at the onset of the pandemic – and in many cases, the criticality of agency missions necessitated the use of Virtual Private Networks (VPNs) as an alternative approach to network access for remote employees. Put simply, a VPN can be used to connect a remote user to a corporate network. More than half (51%) of respondents indicated that their organization’s use of VPNs had increased by 100% or more, and another 35% indicated an increase of at least 50%.
While convenient, using a VPN as a primary workaround for connectivity can introduce more risks than benefits. A well-secured government network, for example, can suddenly be exposed to malware that may have been downloaded inadvertently by a remote user. In many cases, the size of some government agencies and the sheer number of remote users who leveraged a VPN to access the corporate network ultimately resulted in service degradations and interruptions due to bandwidth limitations. This led to users connecting sporadically or failing to connect long enough to receive critical security updates. Not surprisingly, 64% of respondents indicated that their organization’s VPN had performance issues. Risk increased, yet performance decreased.
Malicious adversaries couldn’t have asked for a better opportunity: a massively increased attack surface that was poorly defended by traditional tooling and security approaches. As a result, since the shift to remote work, there has been a significant uptick in VPN attacks and federal advisories about the potential risks of using VPNs.
Cloud First, Cloud Smart, Cloud Secure
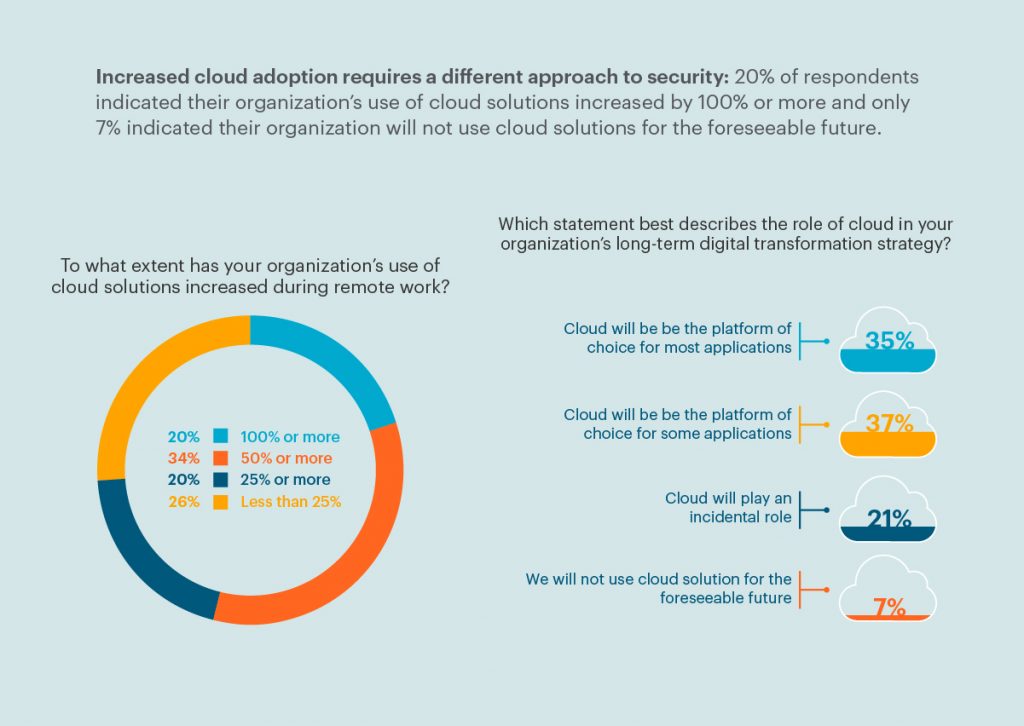
Some agencies turned to the cloud as a workaround to on-prem limitations. Adoption has been gaining momentum in recent years and in 2020, federal cloud spending hit a record high, reaching $6.6 billion. Other surveys have found that roughly half of federal, state, and local governments have some or most systems and solutions in the cloud. Of the respondents in Netskope’s survey, 20% indicated that their organizations’ use of cloud solutions increased by 100% or more due to the shift to remote work, more than 30% indicated that it increased by 50% or more, and another 20% indicated that it increased by 25% or more.
The 2011 Federal IT Modernization Effort included the Cloud First Initiative, which promoted federal cloud adoption but failed to provide specific guidance. Since then, the Office of Management and Budget (OMB) released the Federal Cloud Computing Strategy (Cloud Smart), a more refined successor to the original initiative that includes guidance and key actions for agencies.
When asked about the role of cloud in their organizations’ long-term digital transformation strategy, 37% of respondents indicated that cloud will be the platform of choice for some applications and another 35% reporting that cloud will be the platform of choice for most applications. When these findings are paired against the progress that some organizations are already making, such as the recent 90-day sprint geared towards furthering cloud service adoption that the Office of Personnel Management (OPM) just completed, it’s clear that the old way of working in an on-prem-only environment is now considered legacy. And in terms of security, legacy may as well be synonymous with vulnerable.
The Role of Cloud in a Comprehensive Approach to Security: Zero Trust
Cloud adoption is a critical part of an overall security modernization effort; however, it’s important to recognize the other components that make up a comprehensive, effective approach – and that approach is rooted in data. When government data no longer resides within the traditional perimeter and instead can be accessed remotely by employees – whether by VPN, cloud apps, or some other means – it’s critical that agencies have the ability to truly understand the components in play that could impact the integrity or security of the data, namely, who is attempting to access the data, where they’re accessing the data from, and the state of the device they’re using to attempt access, to name a few.
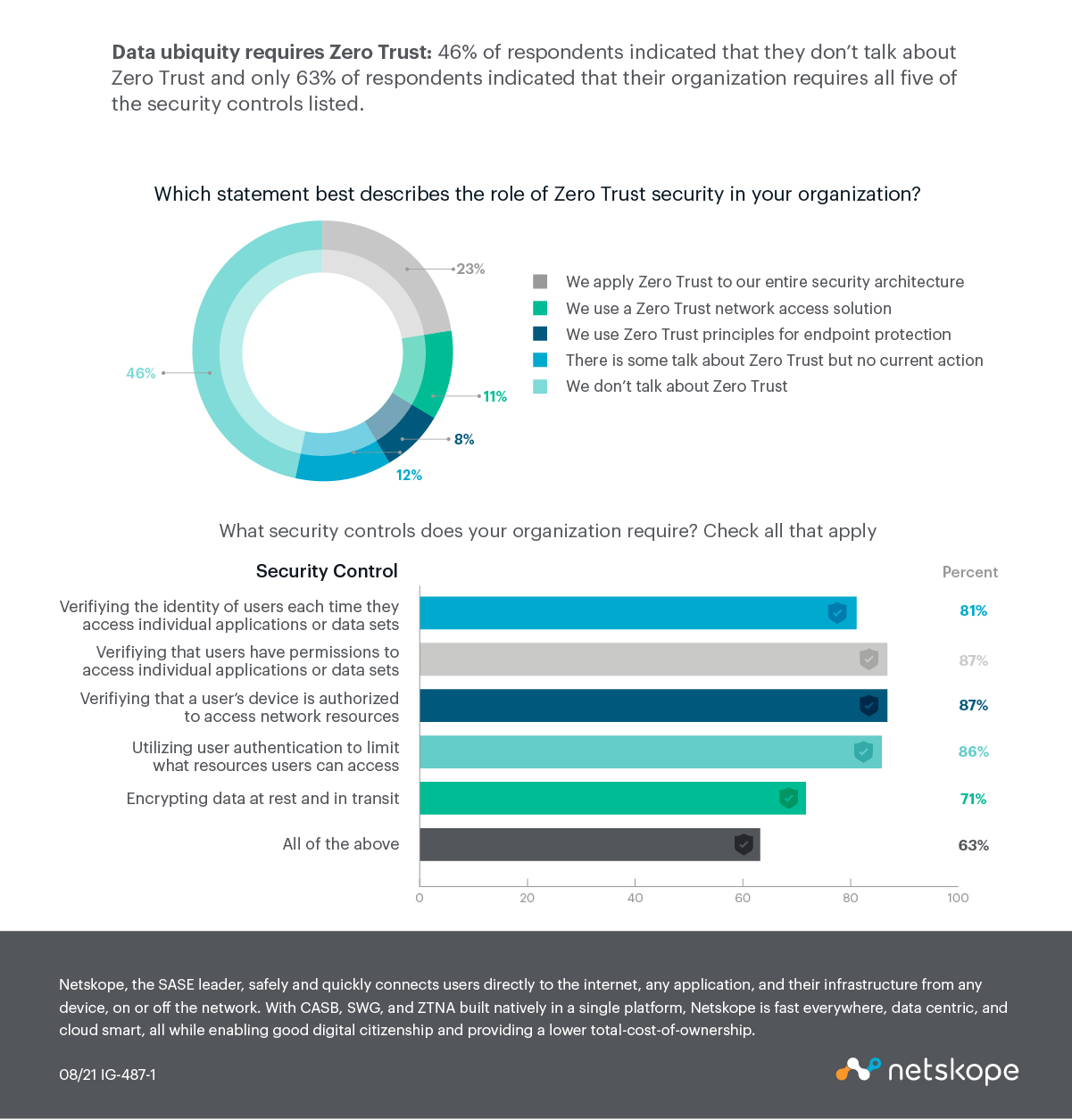
A comprehensive Zero Trust strategy is the most modern and effective means to meet the recently-shifted security needs of federal, state, and local agencies. Because users are connecting to government networks remotely, potentially sensitive government data no longer resides solely within the traditional network perimeter. This data ubiquity requires Zero Trust – an approach that can best be achieved through what Gartner refers to as the Security Service Edge (SSE).
SSE is a more recent term, described by Gartner’s Neil MacDonald and John Watts in the “Hype Cycle(™) for Cloud Security, 2021” in July 2021. SSE secures access to the web, cloud services, and private applications and includes capabilities such as access control, threat protection, data security, security monitoring, and acceptable use control enforced by network-based and API-based integration. In short, it’s the set of capabilities that are required to achieve the level of security that SASE describes, including ZT as a core platform requirement.
Conclusion
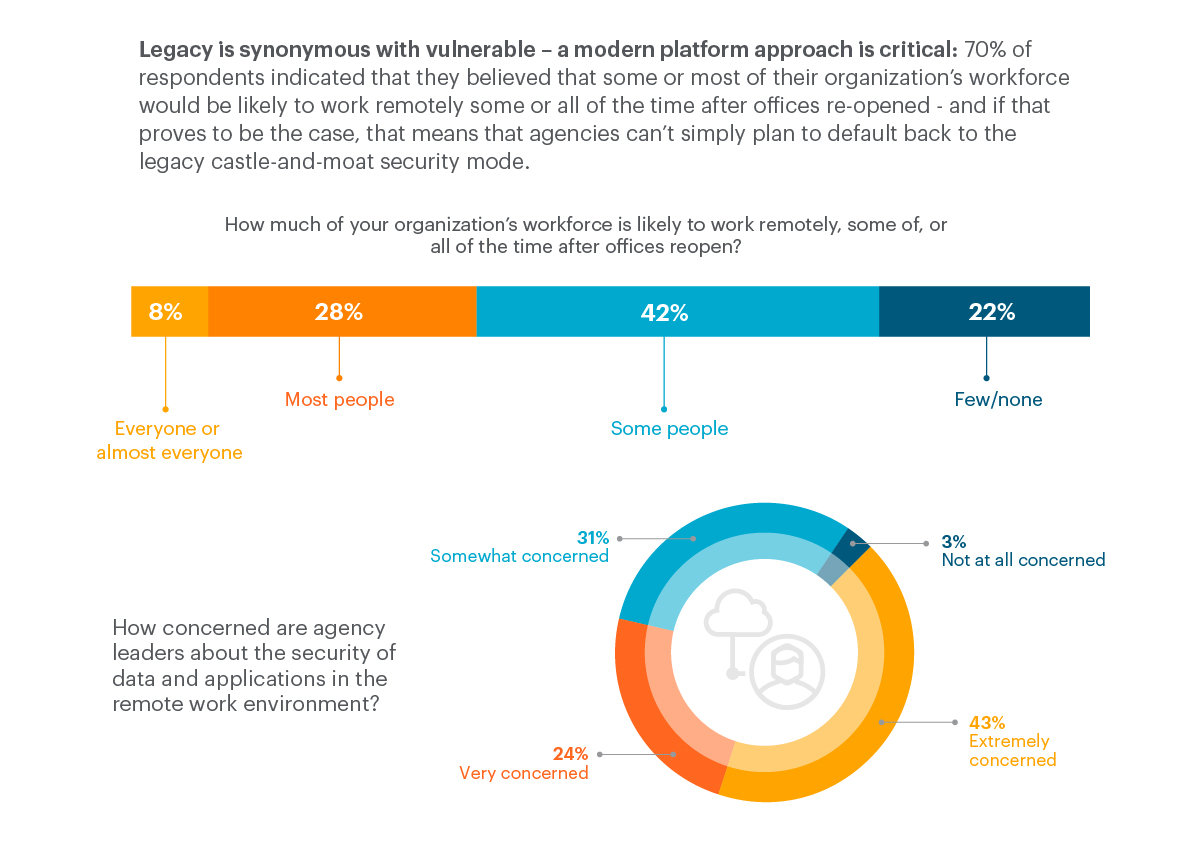
Seventy percent of respondents indicated that they believed that some or most of their organization’s workforce would be likely to work remotely some or all of the time after offices re-opened – and if that proves to be the case, that means that agencies can’t simply plan to default back to the legacy castle-and-moat security model. Agency applications and the data they contain are already outside of the traditional perimeter, so it’s critical that agencies take action to retire traditional on-prem-centric approaches to security and adopt a cloud-smart, data-centric approach to security.
There’s still a long way to go before remote work and security can be mutually inclusive, especially when more than two-thirds of threats are cloud-delivered, so it’s more important than ever before that agencies gain the data and context they need for proper analysis and action – context that can only be provided by a robust, yet nimble platform that enables the journey to SASE, SSE, and ZT. ![]()
You can read the full report here and view the infographic here!
Colby Proffitt



Leave a Comment