Introduction
Managing risks to mission accomplishment is what cybersecurity is all about. Most everyone in a given organization can agree on this as a goal, but getting mission owners, information technology (IT) providers, and security personnel to come together on how it should be done is another matter. Mission owners focus on results: bombs on target, taking care of patients, annual revenue. IT providers focus on enterprise efficiencies, standard solutions, and the latest technologies. Security personnel aim to keep out the bad guys, even if that means inconvenience for end users. And there’s never enough time or money to do it all. How can we bring these groups together to leverage their insights and expertise while balancing competing interests?
Improving the security posture of an enterprise requires adapting not only IT systems, but also the organizations and processes they support. Enterprise architecture (EA) provides the means to align security implementation with enterprise-wide strategic objectives and the shared IT infrastructure that supports the organization.
An EA offers a comprehensive view of an organization, its mission and strategic vision, and the businesses, processes, data, and technology that support it. Although EAs have historically been developed to manage the complexities of systems and their interconnections, they also can be used very effectively to address security controls at the system, process, and enterprise levels. Both civil and defense organizations can benefit from taking an analytical approach to assessing and improving the enterprise’s cybersecurity posture.
What Is Enterprise Architecture?
An EA “is a strategic information asset of an organization. This asset defines the mission of the organization, the behaviors and information necessary to perform the mission, the resources necessary to perform the mission, and the processes for transforming the organization and its resources to satisfy changing mission needs. An EA includes a baseline architecture representing the current organization, a target architecture representing the future organization, and a plan for moving from the present into the future.”1
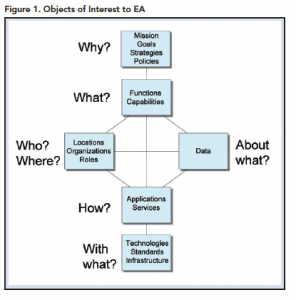 An EA is more than just an inventory of assets; it also captures relationships and dependencies between elements, as shown in Figure 1. Using EA as a tool to maintain and manage these relationships, the organization can achieve two key advantages. First, managers can establish a clear “line of sight” from the organization’s mission and goals to supporting technology and IT services. This informs governance, portfolio management, capital planning, and investment control (CPIC). Activities that do not contribute to the mission of the organization can be identified and their continued funding evaluated. Second, managers can assess the impact of a proposed change by looking at elements related to that change. If a privacy control needs to be applied to certain data elements, the EA can be used to quickly identify functions, organizations, and applications impacted by this change.
An EA is more than just an inventory of assets; it also captures relationships and dependencies between elements, as shown in Figure 1. Using EA as a tool to maintain and manage these relationships, the organization can achieve two key advantages. First, managers can establish a clear “line of sight” from the organization’s mission and goals to supporting technology and IT services. This informs governance, portfolio management, capital planning, and investment control (CPIC). Activities that do not contribute to the mission of the organization can be identified and their continued funding evaluated. Second, managers can assess the impact of a proposed change by looking at elements related to that change. If a privacy control needs to be applied to certain data elements, the EA can be used to quickly identify functions, organizations, and applications impacted by this change.
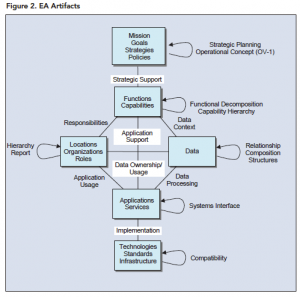 The EA repository maintains this information and can be used to generate EA artifacts, which reflect the relationships between and among enterprise elements. Artifacts are reports or graphical representations of EA elements and their relationships. They include inventories, hierarchies, taxonomies, matrices, wired diagrams, and specialized diagrams, such as process models, data models, or class diagrams. Figure 2 (below) shows a few sample EA artifacts reflecting the relationships between the EA elements of Figure 1. Artifacts are used to analyze EA information to understand the implications of any change.
The EA repository maintains this information and can be used to generate EA artifacts, which reflect the relationships between and among enterprise elements. Artifacts are reports or graphical representations of EA elements and their relationships. They include inventories, hierarchies, taxonomies, matrices, wired diagrams, and specialized diagrams, such as process models, data models, or class diagrams. Figure 2 (below) shows a few sample EA artifacts reflecting the relationships between the EA elements of Figure 1. Artifacts are used to analyze EA information to understand the implications of any change.
Using EA to Improve Cybersecurity
You may have seen EA artifacts used to justify a new IT system acquisition, or to help wallpaper an obscure CIO staff office. EA artifacts can be extended to address security concerns, such as privacy and security controls. The power of enterprise architectures to improve an organization’s cybersecurity posture is realized when EA is used as a common framework for governance as an organization scopes, plans, funds, implements, and tracks cybersecurity activities.
Scoping
An organization is always evolving, so its EA should evolve with it. The EA serves as a common reference for mission owners, IT providers, and security professionals to evaluate the full scope and impacts of specific security concerns. The EA considers security holistically as a business problem, not on a system-by-system basis. When a given threat or vulnerability is considered with respect to an application (or family of applications), the EA helps stakeholders understand what functions these applications support, what data they process, what organizational units use them, and what technology they are using. This provides the organization with a more complete scope of the problem and informs the selection of security controls that balance the concerns of mission owners, IT providers, and security professionals.
Planning and Funding
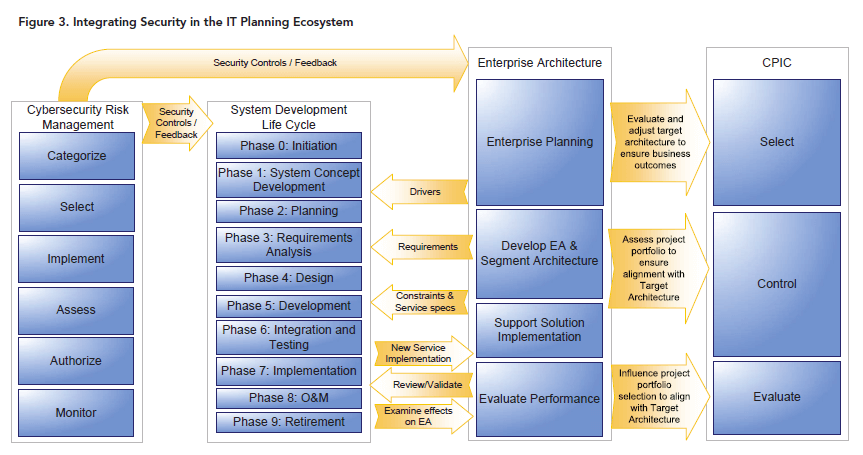
Planning and funding is where an EA can be most beneficial. The EA offers a complete view of an organization that can help define enterprise security approaches and solutions that are more effective and cost-efficient than individual solutions developed for hundreds of applications. At the same time, the operational view that an EA provides can help guard against mission degradation from blind application of a “one size fits all” solution. Security is considered among other business priorities and an EA helps analyze the full effect of proposed controls, while simultaneously justifying investment of limited resources. To accomplish these objectives, EA artifacts can be developed to integrate cybersecurity considerations into the IT planning ecosystem.
What is this ecosystem? To adequately protect information and information assets, security must become part of the organization’s fabric and culture. By integrating strategic planning and CPIC with the information technology program, security investments are better aligned with the organization’s business direction. As shown in Figure 3, security is an integral part of the EA, CPIC, and systems development life cycle (SDLC) ecosystem. The EA ensures that investments align with business direction and helps determine which IT systems are developed and implemented. The EA also influences system development through various drivers, requirements, constraints, and enterprise IT standards.
Implementation
The National Institute of Standards and Technology (NIST) promotes a risk management approach to security. As part of its security program, an organization identifies risks arising from the loss of confidentiality, integrity, or availability of its information. NIST recommends security controls in SP 800-53 as mechanisms that mitigate identified risks.2
But effectiveness depends on the extent to which controls are implemented correctly, operate as intended, and produce the desired outcomes with respect to meeting security requirements for the organization’s data and information systems. Unfortunately, security controls are often implemented in applications without a full understanding of the impact on other applications or on the organization’s business processes.
The EA provides a framework for addressing security, technology, and management problems in an integrated fashion. This framework also fosters discussion between senior leaders and technical staff. It reduces complexity by providing a standard approach to addressing security requirements. Reducing the amount of time spent in the security implementation decision-making process can significantly decrease IT costs, while saving future resources through built-in protection, detection, and reaction capabilities.
Integrating security controls in the enterprise architecture yields two major improvements in the IT planning ecosystem:
- Security drivers (reflecting enterprise approaches and operational considerations) influence system requirements and are considered early in the SDLC. Cybersecurity is “baked in,” not “bolted on.”
- Security solutions can be included in the investment cycle as part of the EA sequencing plan and are prioritized using existing governance processes as shown in the interaction between EA and CPIC in Figure 3.
EA artifacts can be extended to address security concerns, such as privacy and security controls specified in NIST SP 800-53. For example, the implications of the NIST security control AC-2 account management from the access control family might be captured as follows in the different artifacts:
- Description in the enterprise security policy of how account management will be performed
- Inclusion of an account management function in the decomposition of the security function under the IT functional area
- Development of process models on how to perform account management
- Development of a data model for account access
- Construction of matrix organization and roles for applications and systems to specify the authorization of organization or roles for applications.
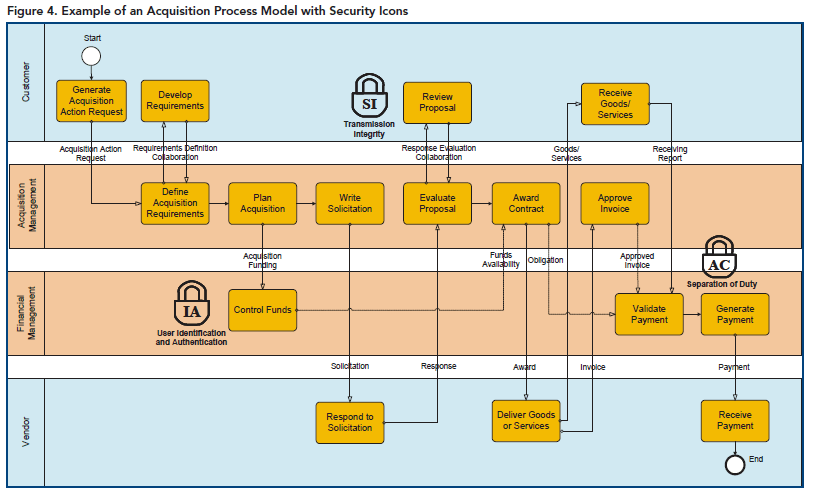
Security controls should be considered in the EA at the enterprise planning stage. Implementation of security controls requires changes and the EA provides artifacts to assess the extent of changes required. New processes may need to be established, or existing ones changed in order to be effective. Additional information may need to be collected and managed. Change often has policy implications that impact how the organization conducts business. Enabling mission owners to specify what control can be implemented increases the likelihood users will use new security policies, procedures, and processes. Figure 4 shows a process model where security controls have been specified at different steps of an acquisition process.
Tracking
Most EA repository tools allow for the customization of the information they store. Thus, EA element objects can be extended to capture relevant security controls. As this information is captured for processes and applications across the enterprise, it becomes feasible to construct queries to identify security gaps and systems that are not in 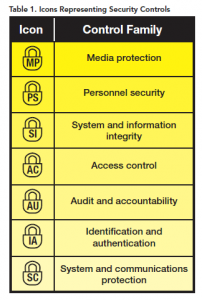 compliance with enterprise cybersecurity standards. The ability to manage the complexity of enterprise security using such powerful tools has tremendous impact. The integration of security in the IT planning ecosystem allows security implementation projects and initiatives to be considered along with the fielding of traditional applications, and their execution can be tracked and evaluated. The EA repository can be extended to manage the security plans for all applications supporting the certification and accreditation process. Querying this repository identifies applications that are not implementing a given security control, thereby facilitating the management of security controls overall.
compliance with enterprise cybersecurity standards. The ability to manage the complexity of enterprise security using such powerful tools has tremendous impact. The integration of security in the IT planning ecosystem allows security implementation projects and initiatives to be considered along with the fielding of traditional applications, and their execution can be tracked and evaluated. The EA repository can be extended to manage the security plans for all applications supporting the certification and accreditation process. Querying this repository identifies applications that are not implementing a given security control, thereby facilitating the management of security controls overall.
Conclusion
Enterprise architectures support the improvement of organizational cybersecurity by providing a common framework to address mission, technology, and security issues. By focusing on mission accomplishment first, cybersecurity is driven from the top down as opposed to the bottom up (which often limits security considerations to the technological or data levels). When employed within an effective governance structure, EAs facilitate executive support and resourcing, thus bringing the full weight of organizational leadership and resourcing to bear.
Sources
- DoD Architecture Framework (DoDAF). DoD Deputy Chief Information Officer, Version 2.02, Change 1, 31 January 2015
- Joint Task Force Transformation Initiative: Security and Privacy Controls for Federal Information Systems and Organizations. National Institute of Standards and Technology SP 800-53, Revision 4. April 2013.



Leave a Comment