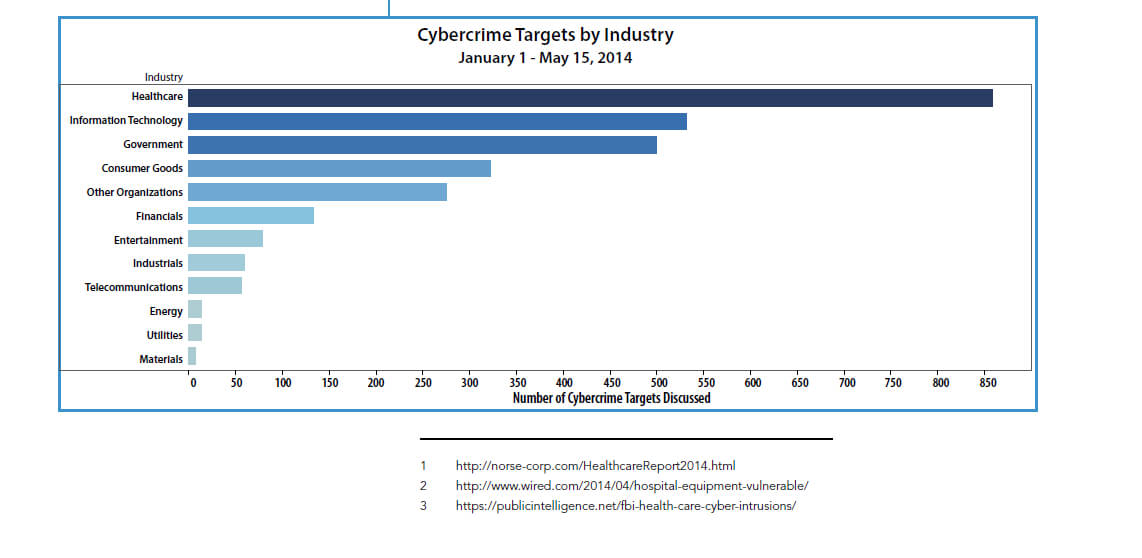
Cybersecurity & Healthcare
Healthcare is a Growing Target for Cybercrime, and It’s Only Going to Get Worse
Author(s):
Jeff Peters, Editor, SurfWatch Labs
2014 is off to a rough start for healthcare when it comes to cybercrime. A SANS-Norse report stated that healthcare organizations are facing an “epidemic of compromises.”1 A two-year study by Essentia Health, which operates roughly 100 facilities in the Midwest, concluded that most hospital equipment is easy to hack.2 And in April the FBI … Read more